Health
How To Make The Most Amazing Candyland Cake
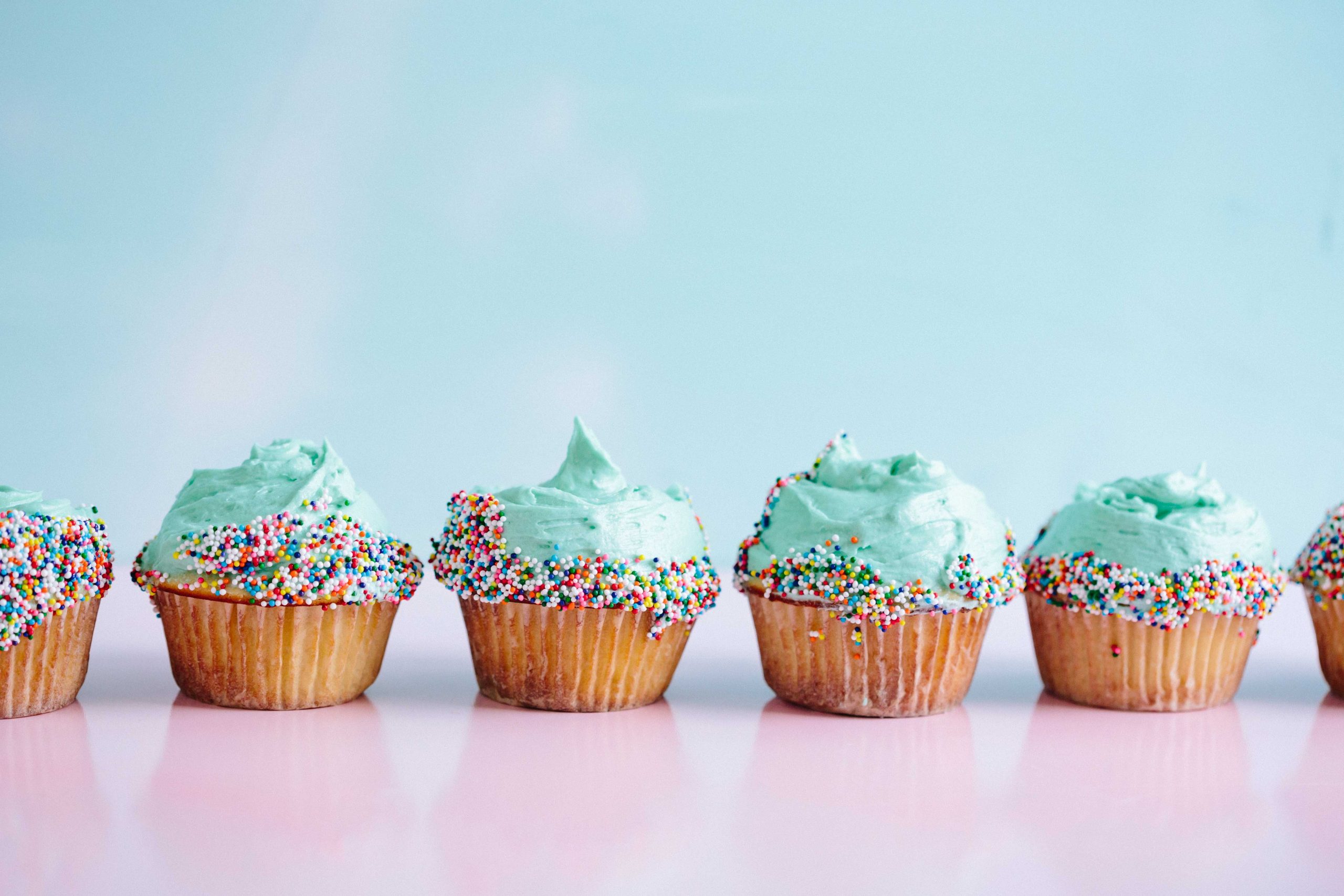
Cake is one of those things that can be enjoyed by everyone, no matter what their dietary restrictions may be. Whether you’re looking for something to celebrate a special occasion or just want to treat yourself, cake is the perfect answer. In this post, we will show you how to make the most amazing Candyland cake. This cake is sure to wow your friends and family, and it’s also a breeze to make. So get ready to get baking!
What You’ll Need
To make this cake, you’ll need:
1 box of cake mix (regular or chocolate)
3 eggs
1 cup vegetable oil
2 cups water
1 cup white sugar
1 teaspoon vanilla extract
24 cups powdered sugar
24 ounces semi sweet chocolate chips
Directions: Preheat oven to 350°F. Grease and flour one 9×13 inch baking dish. In a large bowl, combine cake mix, eggs, vegetable oil, water and white sugar. Mix well and pour batter into prepared baking dish. Bake for 30 minutes or until a toothpick inserted into center comes out clean. Cool on a wire rack for 10 minutes before inverting onto a serving platter. For the frosting: In a medium saucepan over low heat, melt 24 ounces semi sweet chocolate chips with 1/4 cup butter (or margarine). Stir occasionally until melted and smooth. Remove from heat and spread over cake in serving dish. Let frosting set before serving.
How to Make the Cake
Cake-making is a skill that many people want to perfect. The process of making a cake from start to finish can be daunting, but with the right resources and techniques, it can be easy enough for anyone to make. There are many different types of cakes out there, and each one requires a slightly different approach in order to produce an excellent final product. This article will outline the steps necessary for creating the perfect candyland cake.
The first step in any cake-making process is understanding the basics of baking powder and baking soda. These two ingredients are what give cakes their unique texture and flavor. To activate these ingredients, you need only wet them and then pour them into your dry ingredients. Be careful not to overmix these ingredients or you will end up with a tough cake.
Once your Cake mix is together, add oil, eggs, and water according to package directions. Pour this batter into a prepared pan and bake until a toothpick or cake tester comes out clean when inserted into the center of the cake (around 20 minutes). Allow this cake to cool completely before frosting it.
The next step in making this particular cake is preparing the frosting. Candyland Cake is typically frosted with chocolate buttercream so you will need to make that first. In a medium bowl or mixer fitted with an electric mixer, cream together butter and light brown sugar until light and fluffy (about 2 minutes). Add cocoa powder and vanilla extract, mixing until well
How to Make the Frosting
Ingredients:
1 cup (2 sticks) unsalted butter, at room temperature
⅓ cup light corn syrup
2 teaspoons pure vanilla extract
2 cups confectioners’ sugar, sifted
1 teaspoon baking powder
1 teaspoon baking soda
Pinch of salt
Frosting:
6 tablespoons unsalted butter, at room temperature
3 cups confectioners’ sugar, sifted
2 teaspoons pure vanilla extract
How to Assemble the Cake
Cake Assembly:
1. Preheat oven to 350 degrees Fahrenheit. Grease and flour two 9-inch round cake pans. Line the bottoms of the pans with parchment paper and grease the paper.
2. In a medium bowl, combine 1 cup of white sugar, 2/3 cup of all-purpose flour, 2 teaspoons baking powder, 1/4 teaspoon salt, 1/2 teaspoon vanilla extract, and 3/4 cup milk. Mix well to combine and set aside.
3. In a large bowl, cream together 1 cup of butter and 2 cups of white sugar until light and fluffy. Add 3 eggs and mix well to combine. Add 3/4 cup of blackstrap molasses and mix well to combine.
4. Add one quarter of the dry ingredients to the wet ingredients and mix well to combine. Add one third of the blackstrap molasses mixture to the batter mixture and mix well to combine; do not overmix! Pour batter into prepared cake pans, making sure that it fills them evenly.
5. Bake cakes for 30 minutes or until a toothpick or cake tester comes out clean when inserted into the center of each cake layer. Let cakes cool in pan for 5 minutes before removing them from pans to cool completely on wire racks (or serving right away if you prefer). Frosting:
In a large bowl or mixer fitted with an electric mixer on medium speed, beat together 6 cups (or enough cream
How to Store and Serve the Cake
This cake is so good, and it’s definitely a show-stopper! It’s also really simple to make, so it can be a great cake to make for a party.
Ingredients:
Cake:
1 cup (2 sticks) unsalted butter, at room temperature
2 cups granulated sugar
3 large eggs, beaten
2 teaspoons pure vanilla extract
6 cups all-purpose flour
1 teaspoon baking powder
1/2 teaspoon salt
Frosting:
6 ounces cream cheese, at room temperature
1 cup confectioners’ sugar, sifted
1/4 cup milk or heavy cream, plus more as needed
Directions: 1. Preheat oven to 350 degrees F (175 degrees C). Butter and flour an 8×8 inch baking dish. 2. In the bowl of your electric mixer, beat the butter on medium speed until light and fluffy. Add the granulated sugar and continue beating until light and fluffy for about 5 minutes more. 3. With the mixer on low speed, add one egg at a time and mix just until each has been fully incorporated. Stir in the vanilla extract. 4. Add half of the flour mixture to the mixer bowl; beat just until blended. Scrape down the sides of the bowl as needed. Add half of the batter to the prepared baking dish; spread evenly with a spatula or spoon. Sprinkle with coarse sugar crystals (see Note). Bake for 15 minutes until golden
Cake Ingredients
Ingredients:
1 3/4 cups all-purpose flour
3/4 cup unsweetened cocoa powder
2 teaspoons baking soda
1 teaspoon salt
1 1/2 cups (3 sticks) melted butter
2 2/3 cups sugar
6 large eggs, beaten
2 teaspoons vanilla extract
8 ounces cream cheese, softened
16 ounces semi-sweet chocolate chips (2 bags) Directions: Preheat oven to 350 degrees F (175 degrees C). Grease and flour one 9×13 inch baking pan. In a medium bowl, whisk together the flour, cocoa powder, baking soda and salt. In a large bowl, combine the melted butter and sugar until smooth. Add the eggs and vanilla extract; mix well. Pour the batter into the prepared pan. Sprinkle the chocolate chips over the top. Bake for 30 minutes or until golden brown on top. Cool in pan for 10 minutes; then transfer to a wire rack to cool completely
Cake Directions
Ingredients:
1 cup (2 sticks) unsalted butter, at room temperature
2 cups granulated sugar
3 large eggs
2 teaspoons pure vanilla extract
2 cups all-purpose flour
1 teaspoon baking soda
½ teaspoon baking powder
pinch of salt
10 ounces semisweet chocolate, finely chopped (about 2 cups)
10 ounces white chocolate, finely chopped (about 2 cups)
Directions: 1. Preheat oven to 350 degrees F (175 degrees C). Butter and flour two 13×9 inch baking pans. 2. In the bowl of an electric mixer fitted with the paddle attachment, beat butter on medium speed until creamy. Add sugar and beat until light and fluffy. Beat in eggs one at a time, then stir in vanilla extract. 3. In another bowl, whisk together flour, baking soda, baking powder and salt. Gradually add to butter mixture alternately with chocolate until both are fully incorporated. 4. Pour batter into prepared pans and bake for 25 minutes or until a toothpick inserted into the centers comes out clean. Cool in pans for 10 minutes before transferring to a wire rack to cool completely.
Frosting Directions
1. Place the butter and sugar in a saucepan and heat over a low heat until the sugar has melted.
2. Increase the heat to medium and continue to stir until the mixture is smooth.
3. Gradually add the beaten egg, one at a time, stirring constantly until well mixed in.
4. Add the vanilla extract and cream and continue to stir until frosting is smooth and creamy.
5. Pipe frosting onto cake using a piping bag fitted with a star tip or use an electric mixer to beat frosting until smooth.
Decorating and Serving Instructions
Candyland cake is the perfect centerpiece for any party. It’s simple to make and looks great with any decoration you choose. Here are some decorating and serving instructions to help make your cake a success!
To start, prepare your icing by mixing together butter, sugar, vanilla extract, and milk in a bowl until smooth. Add additional milk if desired for a thinner consistency.
Once your icing is ready, set aside one cup of it to use as a “glue” for the cake later on. To make the candy land border, begin by cutting out 10 circles from a green sugar cookie dough (or another color of your choice). Press each circle into the bottom of an 8-inch round cake pan and bake them at 350 degrees Fahrenheit for 8-10 minutes until golden brown. Allow them to cool completely before filling them with your favorite flavored jelly or cream cheese frosting.
For the Candyland castle walls, begin by baking nine yellow sugar cookies according to package instructions. Once they are cooled completely, frost them with royal blue jelly or cream cheese frosting and then cut out 12 small triangle pieces from white chocolate candy bars. Sandwich each triangle between two yellow sugar cookie halves and press against the sides of the cake pan to secure. Once finished, allow the castle walls to cool completely before serving!
This delicious candyland cake is sure to be a hit at any party! Be sure to follow these easy decorating and serving
Health
Yale Navigation Center Ochca: Transforming Lives Through Partnership

Introduction
When someone experiences homelessness or faces a mental health crisis, finding the right support can feel overwhelming. The Yale Navigation Center ochca, in partnership with the Orange County Health Care Agency (OCHCA), serves as a beacon of hope for individuals and families navigating these challenging circumstances.
Located in Orange County, California, this innovative facility represents a collaborative approach to addressing homelessness, mental health services, and substance abuse recovery. The center operates on the principle that comprehensive, coordinated care can break the cycle of homelessness and create lasting positive change in people’s lives.
The partnership between Yale Navigation Center and OCHCA demonstrates how community organizations and government agencies can work together to provide essential services where they’re needed most. This collaboration has transformed how Orange County approaches homelessness services, creating a more streamlined and effective system for those seeking help.
Understanding the Yale Navigation Center’s Mission
The Yale Navigation Center operates as a low-barrier shelter and service hub designed to help individuals transition from homelessness to permanent housing. Unlike traditional shelters, navigation centers focus on providing immediate shelter while simultaneously connecting residents with the resources they need to secure long-term housing solutions.
The center’s approach recognizes that homelessness is often complicated by multiple factors including mental health challenges, substance abuse issues, lack of employment, and absence of social support networks. Rather than addressing these issues separately, the navigation center model provides integrated services under one roof.
This comprehensive approach allows staff members to work closely with each individual to develop personalized action plans. These plans typically include goals related to housing placement, income stabilization, healthcare access, and connection to ongoing support services.
Comprehensive Services at Yale Navigation Center
Emergency Shelter and Housing Services
The Yale Navigation Center provides immediate shelter for individuals who would otherwise be sleeping outdoors. The facility offers beds, meals, and basic amenities while residents work toward securing permanent housing. Unlike many traditional shelters, the center allows couples to stay together and accommodates pets, removing common barriers that prevent people from seeking help.
Housing specialists at the center work directly with residents to identify available housing options, assist with applications, and provide move-in support. This includes helping individuals gather necessary documentation, complete paperwork, and coordinate with landlords and housing authorities.
Mental Health and Behavioral Services
Through its partnership with OCHCA, the Yale Navigation Center provides on-site mental health services including assessment, counseling, and psychiatric care. Licensed mental health professionals are available to help residents address underlying mental health conditions that may have contributed to their homelessness.
The center also offers group therapy sessions, substance abuse counseling, and crisis intervention services. These services are designed to be accessible and culturally sensitive, meeting people where they are in their recovery journey.
Medical Care and Health Services
Basic medical services are available on-site, with more complex medical needs addressed through referrals to OCHCA health centers and community partners. The center provides medication management, health screenings, and treatment for common health issues prevalent among individuals experiencing homelessness.
Residents also receive assistance connecting to health insurance programs including Medi-Cal, ensuring they can access ongoing healthcare services after leaving the center.
Employment and Benefits Assistance
Employment specialists help residents identify job opportunities, develop resumes, and prepare for interviews. The center also provides assistance with obtaining identification documents, Social Security benefits, disability benefits, and other forms of income support.
Computer access and internet connectivity are available to help residents search for jobs, complete online applications, and maintain communication with potential employers and service providers.
The OCHCA Partnership: Strengthening Community Impact
The Orange County Health Care Agency brings significant resources and expertise to the Yale Navigation Center partnership. As the county’s primary healthcare provider for vulnerable populations, OCHCA offers clinical services, care coordination, and connections to the broader county healthcare system.
This partnership allows the navigation center to provide more comprehensive services than would be possible through a single organization. OCHCA’s involvement also ensures that services meet state and county standards for healthcare delivery and that residents receive continuity of care even after leaving the center.
The collaboration extends beyond direct service delivery to include data sharing, outcome tracking, and continuous quality improvement efforts. This systematic approach helps both organizations identify what works best for different populations and adjust services accordingly.
Community Impact and Outcomes
Since opening, the Yale Navigation Center has served hundreds of individuals and families, with many successfully transitioning to permanent housing. The center tracks various outcome measures including housing placement rates, length of stay, returns to homelessness, and connections to ongoing services.
The facility has also contributed to broader community goals by reducing unsheltered homelessness in the surrounding area. By providing immediate shelter and intensive case management services, the center helps people move through the homeless services system more quickly and efficiently.
Community feedback has been generally positive, with local businesses and residents reporting improvements in neighborhood conditions. The center’s good neighbor policies, including regular community meetings and transparent communication, have helped build support for this approach to addressing homelessness.
Success Stories and Real Impact
While individual stories remain confidential, the Yale Navigation Center has documented numerous success cases where residents have achieved stable housing, employment, and improved health outcomes. Many residents arrive at the center after years of cycling through emergency services, temporary shelters, and periods of unsheltered homelessness.
The navigation center model’s effectiveness lies in its ability to provide stability while individuals work on underlying challenges. Rather than having to navigate multiple agencies and locations for different services, residents can focus on their goals while receiving coordinated support.
Some residents have successfully completed substance abuse treatment, reconnected with family members, obtained employment, and secured permanent housing within months of entering the center. These outcomes demonstrate the potential for intensive, coordinated services to create lasting change.
Accessing Yale Navigation Center Services
Individuals seeking services at the Yale Navigation Center typically access the facility through Orange County’s Coordinated Entry System. This system prioritizes individuals based on vulnerability and length of time experiencing homelessness, ensuring that those with the greatest need receive services first.
The center accepts referrals from outreach teams, healthcare providers, law enforcement, and other community organizations. Walk-in assessments may also be available depending on current capacity and staffing.
Potential residents undergo an initial assessment to determine eligibility and develop an initial service plan. The center’s low-barrier approach means that active substance use or mental health symptoms do not disqualify someone from services, though residents are expected to work toward their goals and follow basic community guidelines.
Resources and Contact Information
For individuals seeking services, the best first step is to contact Orange County’s homeless services hotline or visit a local Coordinated Entry access point. Case managers and outreach workers can provide information about current availability and help with the referral process.
Community members interested in supporting the center’s work can explore volunteer opportunities, donation drives, and advocacy efforts. The center regularly needs basic supplies, clothing, and household items for residents preparing to move into permanent housing.
Healthcare providers and social service organizations can partner with the center through referral agreements and collaborative care arrangements. The center welcomes opportunities to coordinate services and share resources with community partners.
Building a Foundation for Lasting Change
The Yale Navigation Center’s partnership with OCHCA represents an innovative approach to addressing homelessness that goes beyond simply providing temporary shelter. By combining immediate assistance with intensive case management and comprehensive services, the center creates opportunities for individuals to address the root causes of their homelessness and build stable, independent lives.
This model demonstrates the importance of collaboration between community organizations and government agencies in addressing complex social challenges. The success of this partnership provides valuable lessons for other communities seeking to develop more effective responses to homelessness.
As Orange County continues to face housing affordability challenges and growing numbers of people experiencing homelessness, facilities like the Yale Navigation Center play a crucial role in the broader solution. The center’s work not only helps individual residents but also contributes to community-wide efforts to prevent and end homelessness.
For those currently experiencing homelessness, the Yale Navigation Center offers hope and practical assistance. For the broader community, it represents a commitment to treating all residents with dignity while working toward effective, long-term solutions to one of our most pressing social challenges.
Frequently Asked Questions
How long can someone stay at the Yale Navigation Center?
Length of stay varies based on individual circumstances and progress toward housing goals. The center works with residents to develop realistic timelines and provides intensive support to help people move to permanent housing as quickly as possible.
Does the Yale Navigation Center charge fees for services?
No, all services at the center are provided free of charge. Residents are not required to pay rent or fees, though they may be expected to contribute to community responsibilities and follow facility guidelines.
Can families stay together at the center?
The center makes efforts to accommodate families whenever possible, though specific policies may depend on available space and facility configuration. Couples are generally able to stay together, and the center welcomes pets.
What happens if someone has a mental health crisis while at the center?
The center has trained staff available 24/7 to respond to mental health crises. On-site mental health professionals can provide immediate assessment and intervention, with connections to emergency psychiatric services if needed.
How can community members support the Yale Navigation Center?
Community support can include volunteering, donating needed items, advocating for homeless services funding, and participating in community education efforts. The yale navigation center ochca maintains relationships with local faith communities, civic organizations, and volunteer groups.
Health
Your Path to Better Health Starts at Minster Chiropractic Center

Introduction
Back pain affects millions of Americans every day, limiting their ability to work, play, and enjoy life to the fullest. If you’re among those seeking relief from chronic pain or looking to improve your overall wellness, Minster Chiropractic Center offers a comprehensive approach to healing that addresses not just your symptoms, but the root causes of your discomfort.
Located in the heart of Minster, our clinic has been serving the community for years with a simple yet powerful mission: to help patients achieve optimal health through natural, non-invasive chiropractic care. We believe that your body has an incredible ability to heal itself when given the right support and environment.
At Minster Chiropractic Center, we understand that every patient is unique. That’s why we take the time to listen to your concerns, thoroughly assess your condition, and create personalized treatment plans that work with your body’s natural healing processes. Whether you’re dealing with acute injury pain or chronic conditions that have persisted for years, our experienced team is here to guide you on your journey to better health.
Understanding Chiropractic Care and Its Life-Changing Benefits
Chiropractic care focuses on diagnosing and treating neuromuscular disorders, with particular emphasis on treating these conditions through manual adjustment and manipulation of the spine. This hands-on approach helps restore proper alignment to your body’s musculoskeletal structure, allowing your body to heal itself without surgery or medication.
The benefits of chiropractic care extend far beyond simple pain relief. Regular chiropractic treatments can improve your posture, enhance your range of motion, and boost your overall energy levels. Many patients report better sleep quality, reduced headaches, and improved athletic performance after beginning chiropractic treatment.
Research has shown that chiropractic care can be particularly effective for treating lower back pain, neck pain, and headaches. The non-invasive nature of these treatments makes them an attractive option for patients who want to avoid prescription medications or surgical procedures. By addressing spinal misalignments and improving nervous system function, chiropractic care supports your body’s natural ability to maintain health and prevent future injuries.
Comprehensive Services Tailored to Your Needs
Spinal Adjustments and Manipulations
Our core service involves precise spinal adjustments designed to correct misalignments in your vertebrae. These adjustments help restore normal motion to spinal joints that aren’t moving properly, reducing pain and improving function. Our skilled chiropractors use various techniques, from traditional manual adjustments to gentler instrument-assisted methods, ensuring that each patient receives care appropriate for their condition and comfort level.
Therapeutic Exercises and Rehabilitation
Recovery doesn’t stop when you leave our office. We provide customized exercise programs designed to strengthen the muscles supporting your spine and prevent future injuries. These exercises are carefully selected based on your specific condition, fitness level, and treatment goals. Our team will teach you proper form and progression, empowering you to take an active role in your recovery.
Soft Tissue Therapies
Muscle tension and scar tissue can contribute significantly to pain and restricted movement. Our soft tissue therapies, including massage therapy and myofascial release techniques, work to relax tight muscles, improve circulation, and promote healing in damaged tissues. These treatments complement spinal adjustments and help achieve longer-lasting results.
Lifestyle and Nutritional Counseling
True wellness encompasses more than just treating symptoms. We provide guidance on ergonomics, posture improvement, and lifestyle modifications that support spinal health. Our nutritional counseling helps you understand how diet affects inflammation and healing, giving you the tools to support your recovery from the inside out.
Real Stories of Transformation and Healing
Sarah, a local teacher, came to us after years of chronic lower back pain that made standing for long periods nearly impossible. After three months of regular treatments and following our exercise recommendations, she returned to full teaching duties pain-free and even started hiking again on weekends.
Mark, a construction worker, suffered a work-related neck injury that left him unable to turn his head without severe pain. Traditional medical treatments provided only temporary relief. Through a combination of spinal adjustments, soft tissue therapy, and targeted exercises, Mark regained full range of motion and returned to work stronger than before.
These success stories reflect what we see daily at Minster Chiropractic Center. While every patient’s journey is different, our commitment to personalized care and comprehensive treatment approaches consistently delivers results that improve quality of life.
Essential Tips for Maintaining Optimal Spinal Health
Practice Good Posture Daily
Whether you’re sitting at a desk or standing in line, maintaining proper posture reduces stress on your spine. Keep your shoulders back, chin tucked, and avoid slouching. If you work at a computer, ensure your monitor is at eye level and take regular breaks to stand and stretch.
Stay Active with Low-Impact Exercise
Regular physical activity keeps your spine flexible and strong. Walking, swimming, and yoga are excellent low-impact options that support spinal health without putting excessive stress on your joints. Aim for at least 30 minutes of activity most days of the week.
Sleep in Spine-Friendly Positions
Your sleeping position can significantly impact spinal alignment. Sleep on your back or side rather than on your stomach, and use pillows to support the natural curves of your spine. A supportive mattress that’s not too soft or too firm will help maintain proper alignment throughout the night.
Lift Objects Properly
Improper lifting technique is a leading cause of back injuries. Always bend at your knees, not your waist, when lifting objects. Keep items close to your body and avoid twisting while lifting. If something is too heavy, ask for help or use mechanical aids.
Starting Your Journey to Better Health
Scheduling your first appointment at Minster Chiropractic Center is simple and convenient. We offer flexible scheduling options to accommodate busy lifestyles, including early morning and evening appointments. During your initial consultation, we’ll conduct a thorough examination, discuss your health history, and explain our recommended treatment approach.
We accept most major insurance plans and offer flexible payment options for those without coverage. Our staff is happy to verify your benefits and help you understand your coverage before your first visit. We believe that financial concerns should never be a barrier to receiving quality healthcare.
New patients can schedule appointments by calling our office directly or using our convenient online booking system. We typically accommodate urgent cases within 24 hours and routine appointments within the same week. Our friendly staff is always available to answer questions about our services, insurance coverage, or scheduling.
Frequently Asked Questions
How many chiropractic sessions will I need?
Treatment length varies depending on your condition, overall health, and treatment goals. Some patients experience significant improvement after just a few sessions, while others with chronic conditions may benefit from longer treatment plans. We’ll discuss expected timelines during your initial consultation and adjust as needed based on your progress.
Is chiropractic treatment safe?
Chiropractic care is considered one of the safest non-invasive treatments for musculoskeletal conditions. Serious complications are extremely rare when treatment is provided by licensed professionals. We always conduct thorough examinations before treatment and modify our approach based on your individual health status.
Will insurance cover my chiropractic care?
Most major insurance plans include chiropractic coverage, though specific benefits vary by policy. Our office staff will verify your coverage and explain your benefits before your first treatment. We also offer affordable cash payment plans for uninsured patients.
What should I expect during my first visit?
Your initial appointment includes a comprehensive health history review, physical examination, and discussion of your treatment goals. We may recommend X-rays if necessary to better understand your condition. Based on our findings, we’ll explain our recommended treatment approach and answer any questions you may have.
Your Health Transformation Starts Today
Living with pain doesn’t have to be your normal. At Minster Chiropractic Center, we’re committed to helping you achieve the healthy, active lifestyle you deserve. Our comprehensive approach to chiropractic care addresses not just your immediate symptoms but also the underlying causes of your discomfort.
Ready to take the first step toward better health? Contact Minster Chiropractic Center today to schedule your consultation. Let us show you how natural, effective chiropractic care can transform your life and help you rediscover the joy of living without pain.
Health
LotterEase: Simplifying Lottery Management for Organizations

Introduction
Managing a lottery or raffle can quickly become overwhelming. Between tracking ticket sales, managing participant data, ensuring compliance with regulations, and conducting fair drawings, organizers often find themselves drowning in administrative tasks. LotterEase emerged as a comprehensive solution designed to streamline these processes, making lottery management accessible for organizations of all sizes.
Whether you’re running a charity fundraiser, organizing a community raffle, or managing corporate prize drawings, the right tools can transform a chaotic process into a smooth operation. LotterEase addresses the common pain points that plague lottery organizers: manual data entry errors, compliance concerns, participant communication challenges, and the complexity of conducting transparent drawings.
This comprehensive guide explores how LotterEase works, its standout features, and the tangible benefits it delivers to organizations seeking efficient lottery management solutions.
How LotterEase Works
LotterEase operates on a user-friendly platform that guides organizers through every stage of lottery management. The system begins with campaign setup, where users define their lottery parameters, including ticket prices, drawing dates, prize structures, and participant eligibility criteria.
Once configured, the platform generates customizable registration forms and ticket purchasing interfaces. Participants can easily purchase tickets online, with the system automatically tracking sales, generating unique ticket numbers, and maintaining comprehensive participant databases.
The platform handles payment processing through secure, integrated payment gateways, ensuring both organizer and participant financial information remains protected. Real-time reporting dashboards provide organizers with instant visibility into sales performance, participant engagement, and revenue generation.
When drawing time arrives, LotterEase employs certified random number generation algorithms to ensure fair, transparent winner selection. The system can accommodate various drawing formats, from simple single-winner raffles to complex multi-tier prize structures.
Key Features of LotterEase
Automated Ticket Management
LotterEase eliminates manual ticket tracking through automated systems that assign unique identifiers to each purchase. The platform maintains real-time inventory counts, preventing overselling while providing organizers with accurate sales data throughout their campaigns.
Compliance Support
Navigating lottery regulations can be complex, varying significantly across jurisdictions. LotterEase includes built-in compliance tools that help organizers understand relevant regulations and maintain required documentation. The platform generates necessary reports and maintains audit trails to support regulatory requirements.
Integrated Communication Tools
Effective participant communication often determines campaign success. LotterEase features automated email systems for purchase confirmations, campaign updates, and winner notifications. Customizable messaging templates ensure consistent, professional communication while saving organizers significant time.
Advanced Analytics
Data-driven insights help optimizers optimize their campaigns. LotterEase provides comprehensive analytics covering sales performance, participant demographics, engagement metrics, and campaign ROI. These insights enable organizers to refine their strategies and improve future campaign effectiveness.
Multi-Channel Sales Support
Modern participants expect purchasing convenience across multiple channels. LotterEase supports online sales, mobile purchasing, and integration with social media platforms, maximizing ticket accessibility and sales potential.
Benefits of Using LotterEase
Time Savings
Organizations report dramatic reductions in administrative time requirements when using LotterEase. Automated processes eliminate manual data entry, reduce communication workload, and streamline winner selection procedures. Many users report saving 10-15 hours per campaign compared to manual management methods.
Increased Revenue Generation
Professional presentation and streamlined purchasing processes typically result in higher participation rates. LotterEase users often see 20-30% increases in ticket sales compared to traditional management approaches, directly translating to improved fundraising results.
Enhanced Credibility
Transparent processes and professional presentation build participant trust. LotterEase’s certified random selection algorithms and comprehensive audit trails provide verifiable fairness, encouraging broader participation and repeat engagement.
Reduced Error Rates
Manual lottery management introduces numerous opportunities for costly mistakes. LotterEase’s automated systems eliminate common errors like duplicate ticket numbers, incorrect winner selections, and miscalculated prize distributions.
Scalability
Whether managing 50 participants or 5,000, LotterEase adapts to campaign size requirements. The platform handles increased participation volumes without requiring additional organizer resources, enabling organizations to grow their fundraising efforts efficiently.
LotterEase Success Stories
Community Sports League
A youth baseball league struggling with annual fundraising implemented LotterEase for their prize raffle campaign. Previous years required extensive volunteer coordination and often resulted in administrative errors. Using LotterEase, they automated their entire process, increased participation by 40%, and raised 35% more funds while reducing volunteer time requirements by 75%.
Nonprofit Healthcare Foundation
A regional healthcare foundation needed to streamline their quarterly charity lottery operations. Manual processes were consuming staff resources and limiting their campaign frequency. LotterEase implementation enabled them to double their campaign frequency while maintaining staff resource levels. Their increased campaign capacity resulted in 60% higher annual fundraising totals.
Corporate Employee Engagement
A technology company wanted to enhance employee engagement through regular prize drawings. Managing these events manually was consuming HR department time and creating scheduling conflicts. LotterEase automation allowed them to increase drawing frequency from monthly to weekly while reducing administrative overhead. Employee participation rates increased by 50% due to improved accessibility and communication.
LotterEase Pricing
LotterEase offers flexible pricing structures designed to accommodate organizations of varying sizes and campaign frequencies. The platform typically provides tiered subscription models based on participant capacity and feature requirements.
Starter plans generally support smaller campaigns with basic features, while professional and enterprise tiers offer advanced analytics, priority support, and unlimited participant capacity. Many pricing structures include transaction-based components, aligning platform costs with campaign success.
Organizations can often access free trials or demo accounts to evaluate platform suitability before committing to subscription plans. Custom pricing arrangements are frequently available for large organizations or those with unique requirements.
Transforming Your Lottery Management Experience
LotterEase represents a significant evolution in lottery management technology, addressing the operational challenges that have traditionally limited organizational fundraising effectiveness. By automating complex processes, ensuring regulatory compliance, and providing professional presentation tools, the platform enables organizations to focus on their core missions while maximizing fundraising potential.
The combination of time savings, increased revenue generation, and reduced administrative burden creates compelling value propositions for organizations considering lottery management solutions. As fundraising competition intensifies and participant expectations continue rising, tools like LotterEase become increasingly essential for maintaining competitive advantage.
Ready to streamline your lottery management process? Consider exploring LotterEase’s trial options to experience firsthand how modern technology can transform your organization’s fundraising capabilities.
Frequently Asked Questions
Is LotterEase suitable for first-time lottery organizers?
Yes, LotterEase is designed with user-friendly interfaces and comprehensive support resources. The platform includes step-by-step guidance and customer support to help new organizers navigate their first campaigns successfully.
How does LotterEase ensure fair winner selection?
LotterEase uses certified random number generation algorithms that meet industry standards for fairness and transparency. The system maintains complete audit trails of all drawing processes, providing verifiable documentation of selection procedures.
Can LotterEase handle multiple concurrent campaigns?
Absolutely. Organizations can manage multiple lottery campaigns simultaneously through the platform, with each campaign maintaining separate participant databases, pricing structures, and drawing schedules.
What payment methods does LotterEase support?
LotterEase integrates with major payment processors, typically supporting credit cards, debit cards, and digital payment platforms. Specific payment options may vary based on geographic location and platform configuration.
Does LotterEase provide customer support during campaigns?
Yes, LotterEase offers customer support services, with response times and availability varying by subscription tier. Higher-tier plans often include priority support and dedicated account management services.
-

 Travel3 years ago
Travel3 years agoNEW ZEALAND VISA FOR ISRAELI AND NORWEGIAN CITIZENS
-

 Technology3 years ago
Technology3 years agoIs Camegle Legit Or A Scam?
-

 Uncategorized3 years ago
Uncategorized3 years agoAMERICAN VISA FOR NORWEGIAN AND JAPANESE CITIZENS
-

 Health3 years ago
Health3 years agoHealth Benefits Of Watermelon
-

 Home Improvement6 months ago
Home Improvement6 months agoArtificial Grass Designs: Perfect Solutions for Urban Backyards
-

 Fashion2 years ago
Fashion2 years agoBest Essentials Hoodies For Cold Weather
-

 Uncategorized3 years ago
Uncategorized3 years agoHow can I write a well-structured blog post?
-

 Fashion11 months ago
Fashion11 months agoGoda Perfume Reviews: Is It Worth Your Investment?














