Health
How To Sharpoint: The Ultimate Guide

There’s no question that a sharp point is the key to success in any number of endeavors. Whether you’re trying to make a great impression at a meeting or simply get your work done faster and easier, having a sharp point can make all the difference. But how do you achieve such a feat? How do you sharpoint? Never fear, dear reader. This guide will show you everything you need to know about how to sharpoint. From the right tools to the perfect technique, by the time you’re finished reading this guide, you’ll be able to achieve sharpness like never before.
What is Sharpoint?
SharePoint is a web-based application that enables businesses to create websites and store documents in a central location. It also allows for collaboration between team members, as well as the ability to share information with customers and partners.
The Different Types of Sharpoint
SharePoint comes in three different versions: Foundation, Standard, and Enterprise. Each version has different features and capabilities.
SharePoint Foundation is the free version of SharePoint. It includes basic document management and collaboration features.
SharePoint Standard is the mid-level version of SharePoint. It includes all the features of Foundation, plus additional features for business intelligence, enterprise content management, and workflow.
SharePoint Enterprise is the top-level version of SharePoint. It includes all the features of Standard, plus additional features for advanced business intelligence, enterprise content management, and workflow.
Pros and Cons of Sharpoint
When it comes to business software, there are a lot of options out there. But one option that is becoming increasingly popular is Microsoft SharePoint. SharePoint is a collaboration and document management platform that can be used for a variety of purposes, from building intranets to creating extranets and public-facing websites.
But like any software, there are both pros and cons to using SharePoint. In this article, we’ll take a look at some of the key pros and cons of using SharePoint so you can decide if it’s the right platform for your business needs.
PROS OF SHAREPOINT:
1. Increased Productivity: One of the main advantages of using SharePoint is that it can help increase productivity levels within an organization. By providing users with a central repository for all their documents and files, they can spend less time searching for information and more time working on actual tasks.
2. Improved Communication and Collaboration: Another big benefit of using SharePoint is that it can help improve communication and collaboration between team members. With features like document libraries and calendaring, team members can easily stay up-to-date on project progress and deadlines.
3. Enhanced Document Management: Another key advantage of using SharePoint is its enhanced document management capabilities. With features like versioning control, check-in/check-out, and approvals, businesses can better manage their documents throughout the entire lifecycle – from creation to expiration.
4. Greater Flexibility and Customization: Another big advantage of using SharePoint is its greater flexibility and customization. Unlike many other business software platforms, SharePoint allows businesses to tailor the platform to their specific needs and preferences. This includes the ability to create custom workflows, forms, and reports.
5. Improved Security: One final advantage of using SharePoint is that it can help improve security for businesses. With features like user permissions and access control, businesses can better control who has access to sensitive information and documents.
CONS OF SHAREPOINT:
1. Requires Training and Upfront Costs: One of the biggest disadvantages of using SharePoint is that it requires training for users in order to get the most out of the platform. Additionally, there are also some upfront costs associated with using SharePoint – such as licenses, hosting fees, and customization costs.
2. Limited Mobile Support: Another downside of using SharePoint is that its mobile support is limited compared to other business software platforms. While there are some mobile apps available, they don’t offer the same level of functionality as the desktop version of SharePoint.
3. Complex Interface: One final disadvantage of using SharePoint
What Foods to Eat on Sharpoint?
When it comes to following the Sharpoint diet, there are certain foods that you should definitely include in your diet plan. These foods have been shown to help improve gut health and promote weight loss.
Some of the best foods to eat on Sharpoint include:
1. Fermented Foods: Fermented foods like yogurt, kimchi, and sauerkraut are rich in probiotics which have been shown to improve gut health. Probiotics can also help boost your immune system and fight off infection.
2. Fiber-Rich Foods: Foods that are high in fiber help keep you feeling full and can aid in weight loss. Good sources of fiber include fruits, vegetables, whole grains, and beans.
3. Healthy Fats: Healthy fats like olive oil, avocados, and nuts are important for keeping your body fueled and helping you lose weight. healthy fats can also help improve your cholesterol levels and lower your risk for heart disease.
4. Protein: Protein is essential for building muscle and losing weight. Good sources of protein include lean meats, fish, tofu, and legumes.
Recipes for Sharpoint
If you’re looking for some recipes to help you get the most out of your Sharpoint experience, look no further! Here are some of our favorite recipes to help you make the most of yourSharpoint:
-Sharpoint Salad: This salad is a great way to get your daily dose of Sharpoint, and it’s perfect for a light lunch or side dish. Simply mix together some chopped lettuce, tomatoes, cucumbers, and feta cheese, and dress with your favorite vinaigrette. Add a few slices of Sharpoint on top, and you’re good to go!
-Sharpoint Toast: This is a simple but delicious way to enjoy Sharpoint. Just spread some Sharpoint on a piece of toast, and add your favorite toppings. We like ours with avocado and tomato, but feel free to get creative!
-Sharpoint Smoothie: Start your day off right with this nutritious smoothie. Simply combine Sharpoint with milk or yogurt, fruit (we love banana and berries), and a touch of honey or agave nectar. Blend until smooth, pour into a glass, and enjoy.
Alternatives to Sharpoint
If you’re looking for alternatives to Sharpoint, there are a few options out there. One popular alternative is Google Drive, which offers a lot of the same features as Sharpoint. Another option is Office 365, which is a subscription-based service that includes access to Microsoft Office apps and other productivity tools. There are also a number of free online storage services, such as Dropbox and Box.net, that can be used for storing and sharing files.
Conclusion
We hope this guide has been helpful in teaching you how to sharpoint. Remember, the key is to keep practicing and to never give up. With a little bit of time and effort, you’ll be a sharpointing pro in no time.
Read more about How To Sharpoint: The Ultimate Guide
Health
THC Shooters vs. CBD Shots: What’s the Difference?
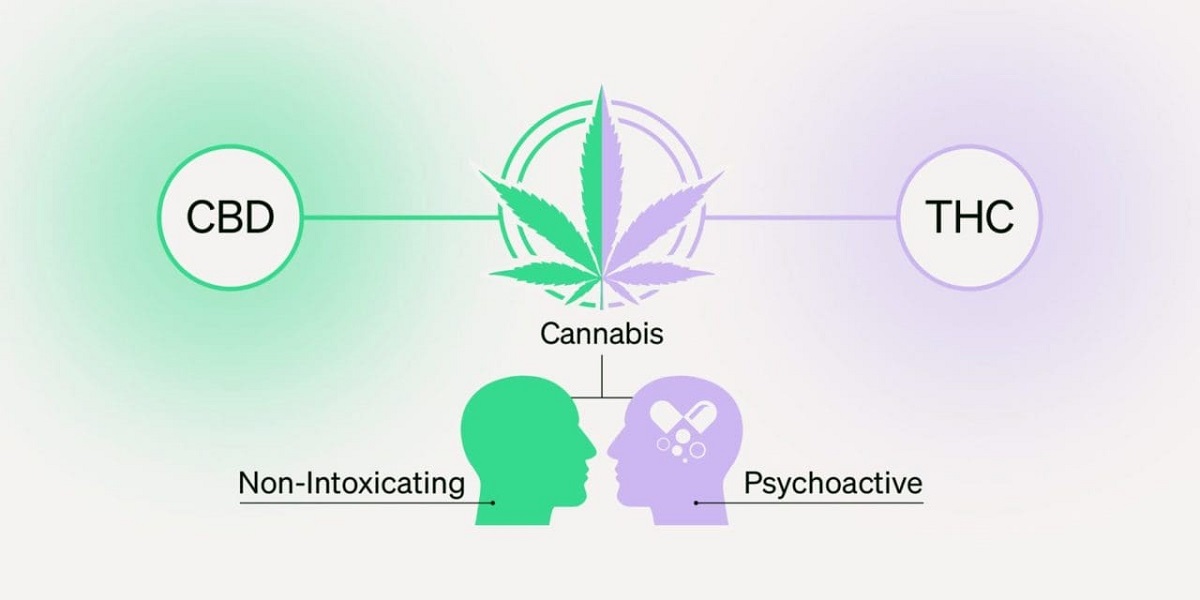
The cannabis and hemp industry has seen massive innovation over the past few years, with new products designed to meet the diverse needs of consumers. Among the most popular and convenient options are THC Shooters and CBD shots. While these beverages may look similar in size and packaging, their effects, uses, and legal standing are very different. For anyone exploring cannabis or hemp products, understanding the distinction between THC and CBD shots is essential to making an informed choice.
What Are THC Shooters?
THC Shooters are small, concentrated cannabis-infused drinks that contain tetrahydrocannabinol (THC), the primary psychoactive compound in cannabis. Unlike smoking or vaping, shooters provide a discreet and easy way to consume THC without inhalation. These products typically come in small bottles often 2 to 4 ounces allowing users to quickly consume a precise dose.
The main appeal of THC Shooters lies in their potency and fast-acting effects. Since they are liquid-based, the body can absorb THC more quickly than traditional edibles, such as gummies or baked goods. This makes shooters a preferred option for recreational consumers seeking an uplifting or euphoric experience. Depending on the dosage, they can provide feelings of relaxation, creativity, or even heightened sensory awareness.
What Are CBD Shots?
CBD shots, on the other hand, are small beverages infused with cannabidiol (CBD), a non-psychoactive compound derived from hemp or cannabis plants. Unlike THC, CBD does not produce a “high.” Instead, it interacts with the body’s endocannabinoid system to promote balance and wellness.
These shots are often marketed as wellness supplements rather than recreational products. They can be infused with additional ingredients like vitamins, adaptogens, or natural flavors to enhance relaxation, focus, or energy. CBD shots are popular among people who want the therapeutic benefits of cannabis without intoxication.
The Key Differences Between THC Shooters and CBD Shots
1. Psychoactive Effects
The most obvious difference is the effect on the mind. THC Shooters deliver a psychoactive experience, which may range from mild relaxation to a strong euphoric “high.” CBD shots, however, are non-intoxicating and primarily focus on wellness benefits like stress relief, reduced anxiety, or improved sleep.
2. Legal Considerations
In regions where recreational or medical cannabis is legal, THC-based products like shooters are widely available. However, in places where cannabis remains restricted, they may be illegal. CBD shots, derived from hemp containing less than 0.3% THC, are federally legal in many areas, making them easier to access.
3. Usage Purposes
THC Shooters are often chosen for recreational enjoyment, creative stimulation, or social experiences. CBD shots are typically used by individuals seeking natural relief from issues like inflammation, anxiety, or fatigue without impairing mental clarity.
4. Duration and Onset
Both THC and CBD shots act faster than traditional edibles due to their liquid form. THC effects are often felt within 20–40 minutes and can last several hours. CBD shots also provide relatively quick relief but without the intense “ride” associated with THC.
Who Should Choose THC Shooters?
THC Shooters are ideal for adults in legal markets who want to experience the psychoactive effects of cannabis in a convenient, discreet form. They’re also a great choice for social events or for those who prefer not to smoke. Since shooters can be quite potent, beginners should start with smaller doses to avoid overwhelming effects.
Who Should Choose CBD Shots?
CBD shots are best suited for individuals looking to enhance their wellness routine without altering their mental state. They are popular among busy professionals, athletes, or anyone interested in natural ways to manage stress, pain, or sleep challenges. Since they are non-intoxicating, CBD shots can be consumed at any time of day, even during work hours.
The Growing Popularity of Cannabis Beverages
Both THC Shooters and CBD shots are part of the growing cannabis beverage trend. Consumers are increasingly drawn to drinks because they are portable, discreet, and offer more predictable dosing compared to traditional edibles. The convenience of a “grab-and-go” wellness or recreational shot makes them appealing to both newcomers and seasoned cannabis users.
Conclusion
When comparing THC Shooters and CBD shots, the choice ultimately depends on personal goals. If you are seeking a euphoric, psychoactive experience, shooters infused with THC are the right option provided you are in a legal market and consume responsibly. If your focus is on health, balance, and relaxation without intoxication, CBD shots may be more suitable.
As cannabis beverages continue to evolve, both THC and CBD shots will likely remain popular, serving two very distinct audiences: one seeking recreational enjoyment and the other prioritizing wellness and calm. By understanding the differences, consumers can confidently choose the product that best matches their lifestyle and needs.
Health
PCV Oil Catch Can 2007 Ford F150 5.4LIT– Complete Guide

Introduction
If you drive a 2007 Ford F-150 with the 5.4L engine, you know it’s a reliable truck. It’s tough, powerful, and built for work or family use. But like any vehicle, it has weak spots. One of those is the buildup of oil vapors in the intake system.
This is where a PCV oil catch can comes in. Installing a catch can on your 2007 Ford F-150 5.4L helps reduce carbon buildup, keeps the intake cleaner, and improves long-term performance. Many truck owners overlook this upgrade, but it can make a big difference in engine health.
In this guide, we’ll explain what a PCV oil catch can does, why it’s important, and how you can install and maintain one. We’ll also share real owner experiences, common mistakes, and practical tips to help you get the most out of your Ford.
What Is a PCV Oil Catch Can?
A PCV oil catch can is a small device connected to your truck’s positive crankcase ventilation (PCV) system. The PCV system takes gases and oil vapors from inside the engine and routes them back into the intake. This helps reduce emissions.
The problem is that along with air, the system pulls in tiny oil droplets. Over time, those droplets build up inside the intake manifold and throttle body. This can lead to carbon deposits, sticky valves, and reduced performance.
The oil catch can solves this problem. It traps those oil vapors before they reach the intake. Clean air flows through, but oil and gunk get caught in the can. That means less buildup, a cleaner engine, and longer life for your 5.4L motor.
Why Your 2007 Ford F-150 5.4L Needs One
The 2007 Ford F-150 with the 5.4L Triton V8 is known for power, but it also has issues with carbon buildup. Over time, oil deposits in the intake can cause rough idling, hesitation, and even loss of horsepower.
Installing a PCV oil catch can helps reduce these problems. It keeps the air going into your engine cleaner, which means smoother combustion. Owners often report that their trucks run better, idle smoother, and even get a small bump in fuel economy.
Another reason your F-150 needs a catch can is longevity. When your intake valves stay clean, your engine doesn’t have to work as hard. That reduces wear and tear, which helps your truck last longer. For a vehicle as valuable as a Ford F-150, this is a smart investment.
How the PCV System Works in Your Truck
To understand why a catch can matters, it helps to know how the PCV system works.
When your engine runs, pressure builds inside the crankcase. Without a way to vent it, that pressure could damage seals or cause leaks. The PCV valve solves this by allowing gases and vapors to escape. These gases are sent back into the intake so they can be burned again.
On paper, this is a good system. It reduces emissions and keeps your engine efficient. But it’s not perfect. Oil mist often rides along with the gases. In a 2007 F-150 5.4L, this oil mist can collect on intake valves, spark plugs, and sensors. That’s where a pcv oil catch can 2007 ford f150 5.4lit can makes a big difference by filtering out that unwanted oil.
Common Problems Without an Oil Catch Can
If you don’t use a catch can, your 2007 Ford F-150 5.4L may develop several issues over time:
-
Carbon buildup on intake valves
-
Reduced performance and sluggish acceleration
-
Poor fuel economy due to dirty combustion
-
Check engine lights from fouled sensors
-
Oil pooling inside the intake manifold
Some owners even report having to clean their intake system more often, which costs time and money. The Triton V8 is strong, but like many engines, it doesn’t like running on dirty air. That’s why an oil catch can is a smart preventative step.
Benefits of Installing a Catch Can on a 5.4L Engine
Adding a PCV oil catch can to your 2007 Ford F-150 5.4L brings several clear benefits:
-
Cleaner intake system – Less carbon buildup means smoother airflow.
-
Better fuel economy – Cleaner combustion helps you get more miles per gallon.
-
Longer engine life – Reducing gunk protects valves and pistons.
-
Improved performance – Many owners feel better throttle response.
-
Lower maintenance costs – Fewer cleanings and fewer repairs over time.
Think of it like a filter for your engine’s breathing system. You wouldn’t drive without an air filter, so why let oil mist clog up your intake?
Choosing the Right Oil Catch Can for Your Ford F-150
Not all oil catch cans are the same. When shopping for one, look for these features:
-
Quality materials: Aluminum cans last longer than plastic ones.
-
Baffled design: Helps trap more oil and vapors.
-
Easy drain system: A drain valve makes emptying faster.
-
Direct fit kits: Some are made specifically for Ford F-150 trucks.
Popular brands among F-150 owners include JLT, Mishimoto, and UPR. While universal catch cans are cheaper, a kit designed for the 2007 F-150 5.4L will fit better and look cleaner under the hood.
Step-by-Step Guide to Installing a Catch Can
Installing a catch can on your 2007 Ford F-150 5.4L is a straightforward project. Here’s a simple guide:
-
Locate the PCV hose – It usually runs from the valve cover to the intake.
-
Remove the hose – Gently disconnect it from both ends.
-
Mount the catch can – Find a secure spot in the engine bay.
-
Connect new hoses – Route one from the PCV valve to the can, and another from the can to the intake.
-
Secure with clamps – Make sure everything is tight and leak-free.
-
Check for clearance – Ensure hoses don’t rub against moving parts.
Most installs take about an hour with basic tools. If you’re not comfortable, any mechanic can do it quickly.
Maintenance Tips for Long-Lasting Performance
A catch can is low-maintenance, but it does need attention. Here’s how to keep it working:
-
Empty the can regularly – Every 1,000–3,000 miles, depending on driving style.
-
Check hoses and fittings – Make sure nothing is loose.
-
Clean the can – Wipe out residue every few oil changes.
-
Monitor oil levels – A catch can won’t affect your dipstick reading much, but always double-check.
With regular care, your oil catch can will keep protecting your Ford F-150 for years.
Real-World Results: Owners’ Experiences
Many 2007 Ford F-150 5.4L owners who install a catch can report positive results. Common feedback includes:
-
Noticeably cleaner intake manifolds during inspections
-
Less oil smell in the engine bay
-
Improved throttle response and smoother idling
-
Longer intervals between needing intake cleanings
One owner even mentioned that after installing a catch can at 100,000 miles, his truck’s idle became steadier, and spark plugs lasted longer than before. Real-world use proves that catch cans aren’t just hype they deliver results.
Mistakes to Avoid When Using a Catch Can
While catch cans are helpful, there are a few common mistakes:
-
Not emptying it – A full can can’t catch more oil.
-
Poor mounting – Loose cans may rattle or cause leaks.
-
Cheap hoses – Weak hoses can collapse under vacuum pressure.
-
Wrong routing – Reversing the hoses means it won’t work properly.
Avoiding these mistakes ensures your catch can does its job correctly and keeps your F-150 running strong.
Cost vs. Value: Is It Worth It?
A quality oil catch can costs between $100–$200, plus installation if you don’t DIY. That may sound like a lot for a small part, but consider the savings:
-
Intake cleanings can cost $300+
-
Repairs for fouled valves or sensors can cost even more
-
Better fuel economy saves money at the pump
When you look at it this way, a catch can is an affordable insurance policy for your 2007 Ford F-150 5.4L.
Alternatives to Oil Catch Cans (and Why They Fall Short)
Some people ask if fuel additives or regular cleanings can replace a catch can. While these help, they don’t stop oil from entering the intake in the first place. Additives may clean some buildup, but prevention is better.
Another alternative is deleting the PCV system, but this isn’t recommended. It can cause pressure issues, oil leaks, and even legal problems since it removes an emissions system.
In short, nothing replaces the consistent protection of a well-installed oil catch can.
Frequently Asked Questions
1. What does a PCV oil catch can do for my Ford F-150?
It traps oil vapors before they reach your intake, keeping it cleaner and improving performance.
2. Will installing a catch can void my warranty?
No, a catch can doesn’t harm your engine. It’s a simple add-on. Still, always check with your dealer.
3. How often should I empty my oil catch can?
Most owners empty it every 1,000–3,000 miles, but it depends on driving conditions.
4. Is a catch can hard to install on a 2007 F-150 5.4L?
Not at all. Most people can install one with basic tools in about an hour.
5. What’s the best oil catch can brand for Ford trucks?
Popular brands include Mishimoto, JLT, and UPR. Choose one designed for your F-150.
6. Can I drive without a catch can?
Yes, but you’ll likely face more carbon buildup and intake cleaning over time.
Conclusion
Your 2007 Ford F-150 5.4L is built tough, but even tough engines need a little extra care. A PCV oil catch can is a simple, affordable upgrade that protects your intake system, improves performance, and extends engine life.
By catching oil before it causes buildup, you save time, money, and headaches down the road. Whether you’re hauling, commuting, or just enjoying your truck, an oil catch can helps it run cleaner and stronger.
If you haven’t installed one yet, now’s the time. Protect your Ford, keep it running like new, and enjoy every mile with confidence.
Health
When Were Lobotomies Made Illegal? A Deep Dive Into History, Science, and Ethics

Introduction
If you’ve ever wondered, “When were lobotomies made illegal?”, you’re not alone. The lobotomy is one of the most shocking and controversial procedures in medical history. Once seen as a miracle cure for mental illness, it later became a symbol of medical overreach and ethical failure.
This article takes you on a journey through the origins of lobotomies, why doctors thought they worked, the painful stories behind them, and how the world finally turned against the practice. We’ll explore not just when lobotomies were made illegal, but also why they fell out of favor, what replaced them, and what lessons we can learn today.
So grab a cup of coffee, sit back, and let’s uncover the truth about this dark yet fascinating chapter of medicine.
What Exactly Is a Lobotomy?
A lobotomy is a surgical procedure where doctors cut or damage parts of the brain’s frontal lobes. The idea was simple: if mental illness came from overactive brain circuits, then damaging those circuits might “calm” the patient.
The procedure became popular in the 1930s and 1940s. Portuguese neurologist António Egas Moniz developed the first version, earning him the 1949 Nobel Prize. Soon after, American psychiatrist Walter Freeman made lobotomies famous in the United States with his faster, cheaper “ice-pick” method.
At first, lobotomies were hailed as groundbreaking. Patients who had been locked away in asylums sometimes appeared calmer afterward. But the results came at a terrible cost personality changes, permanent disability, and in many cases, death.
Why Did Doctors Think Lobotomies Were Helpful?
Back then, mental illness treatments were limited. There were no antidepressants, no modern therapy, and very few effective medications. Asylums were overcrowded, and families were desperate.
Lobotomies promised a quick solution. Patients who had been violent or distressed often became quiet. To doctors in the mid-20th century, this seemed like success. In fact, thousands of lobotomies were performed in the U.S., especially in state hospitals.
However, what doctors saw as “calm” was often just a loss of personality, independence, and cognitive function. Families noticed their loved ones came back “different” sometimes childlike, emotionless, or unable to care for themselves.
This gap between medical hope and human suffering is one reason the world later asked: when were lobotomies made illegal?
The Rise of the Ice-Pick Lobotomy
Walter Freeman was not a surgeon but a psychiatrist. Still, he popularized the transorbital lobotomy, also known as the “ice-pick” method. With an actual ice-pick-like tool, Freeman would push through the eye socket into the brain, severing connections.
He performed the procedure in his office, in hospitals, and even on tours across America. Freeman believed lobotomies could treat depression, schizophrenia, anxiety, and even simple nervousness.
At the peak of the lobotomy craze, nearly 40,000 Americans underwent the procedure. Some were willing, others were not. Even children were lobotomized. One of the most famous cases was Rosemary Kennedy, sister of President John F. Kennedy, whose lobotomy left her severely disabled for life.
The Turning Point: When Public Opinion Shifted
The tide began to turn in the 1950s. Several key developments changed how people viewed lobotomies:
-
Tragic outcomes became known – Stories of patients who were permanently harmed began to spread.
-
Medical ethics improved – Doctors faced more accountability for experimental treatments.
-
New medications appeared – Antipsychotic drugs like chlorpromazine offered safer, non-surgical alternatives.
By the 1960s, lobotomies were widely criticized. Journalists, families, and even other doctors spoke out. The question of when were lobotomies made illegal became urgent, as governments debated whether to ban the practice outright.
So, When Were Lobotomies Made Illegal?
Here’s the surprising truth: lobotomies were never officially banned in every country at the same time. Instead, their use declined gradually due to public outrage and better treatments.
-
United States: Lobotomies largely ended in the late 1960s and 1970s. No federal law banned them outright, but medical standards made the practice unacceptable.
-
United Kingdom: The Mental Health Act of 1983 required special permission for psychosurgery, effectively ending lobotomies.
-
Other countries: Most European nations phased out lobotomies between the 1970s and 1980s, though some procedures lingered.
So, the answer to “When were lobotomies made illegal?” is complex. They weren’t suddenly outlawed everywhere, but instead became seen as unethical, dangerous, and outdated.
The Role of Medication in Ending Lobotomies
One of the biggest reasons lobotomies disappeared was the rise of psychiatric drugs. In the 1950s, medications like Thorazine (chlorpromazine) gave doctors new ways to treat severe mental illness.
These drugs didn’t require surgery, didn’t cause brain damage, and were much safer overall. Hospitals quickly adopted them, and lobotomy numbers dropped. Patients who might once have been operated on now received medication and therapy instead.
This shift shows how medical progress can save lives. The introduction of better treatments answered the question not just of when lobotomies were made illegal, but why they became unnecessary.
Famous Cases That Changed Public Perception
The tragic story of Rosemary Kennedy is perhaps the most famous lobotomy case. Her surgery in 1941 left her permanently incapacitated, shocking the Kennedy family and later the public.
Other notable cases included celebrities like playwright Tennessee Williams’ sister, Rose, who also underwent a lobotomy. Countless unnamed patients in psychiatric hospitals suffered the same fate.
These personal stories fueled outrage. They made people realize lobotomies were not a miracle cure but a risky experiment on vulnerable people. By the 1970s, the pressure to stop lobotomies grew stronger than ever.
The Ethical Lessons of Lobotomies
The story of lobotomies isn’t just medical history it’s also a lesson in ethics. Doctors once thought they were helping, but their methods caused harm. Patients often couldn’t give informed consent, and many procedures were done without full understanding of the risks.
Today, medical ethics emphasize patient rights, informed consent, and evidence-based treatments. The painful question of when lobotomies were made illegal reminds us why these rules are so important.
Are Lobotomies Still Performed Today?
In most of the world, lobotomies are no longer performed. However, a modern and very different procedure called psychosurgery still exists in rare cases. For example, deep brain stimulation or cingulotomy may be used to treat severe, treatment-resistant conditions like OCD.
These modern surgeries are highly controlled, ethical, and performed only when all other treatments fail. They are nothing like the crude lobotomies of the past.
So while lobotomies as we know them are gone, their history continues to shape how medicine approaches mental health.
What Replaced Lobotomies in Mental Health Care?
The end of lobotomies didn’t mean the end of treatment. Instead, mental health care expanded in healthier ways:
-
Medication: Antidepressants, antipsychotics, and mood stabilizers became standard.
-
Therapy: Talk therapy, cognitive-behavioral therapy (CBT), and family counseling grew popular.
-
Community care: Many patients left large institutions for outpatient and community-based support.
This new approach gave people dignity, choice, and better results. It shows why asking when lobotomies were made illegal is really about understanding how far mental health care has come.
The Cultural Impact of Lobotomies
Lobotomies left a mark not just on medicine but on culture. Books, movies, and documentaries often reference them as symbols of medical cruelty. One Flew Over the Cuckoo’s Nest is one of the most famous examples, showing the lobotomy as a punishment for nonconformity.
These cultural portrayals kept public memory alive, ensuring lobotomies would not quietly fade into history. Instead, they became a cautionary tale about the dangers of unchecked medical power.
Lessons for Today’s Mental Health Care
Looking back, the lobotomy era teaches us several lessons:
-
Desperation can lead to risky solutions.
-
New treatments must be tested carefully before being widely adopted.
-
Patient rights should always come first.
-
Hope should never replace evidence.
These lessons help guide today’s medical professionals. They remind us that when we ask when lobotomies were made illegal, we’re also asking how to prevent similar mistakes in the future.
FAQs About Lobotomies
1. When were lobotomies made illegal in the United States?
They were never formally outlawed nationwide but fell out of practice by the late 1960s–1970s due to ethical concerns and better treatments.
2. Did any country officially ban lobotomies?
Yes, some countries placed strict legal restrictions. For example, the UK’s Mental Health Act of 1983 required approval before psychosurgery.
3. How many people had lobotomies?
Around 40,000 in the United States and more than 50,000 worldwide underwent lobotomies before the practice ended.
4. Did lobotomies ever actually work?
Some patients became calmer, but most suffered severe side effects, including personality loss, disability, or death.
5. Are lobotomies and psychosurgery the same thing?
No. Lobotomies were crude brain cuts, while modern psychosurgery uses advanced, targeted methods and strict ethics.
6. Why do people still ask “when were lobotomies made illegal”?
Because the practice was never banned everywhere at once, the timeline varies by country, making it a complex historical question.
Conclusion: Why This History Still Matters
So, when were lobotomies made illegal? The real answer is that they were never fully outlawed in every place at once. Instead, they slowly disappeared as society recognized the harm they caused and embraced safer, more compassionate treatments.
The story of lobotomies is a warning about what happens when desperation outruns science. It shows the importance of ethics, patient rights, and constant learning in medicine.
As we continue to face mental health challenges today, remembering this history helps us stay humble, careful, and hopeful. After all, medicine is not just about curing illness it’s about protecting human dignity.
-

 Technology3 years ago
Technology3 years agoIs Camegle Legit Or A Scam?
-

 Travel3 years ago
Travel3 years agoNEW ZEALAND VISA FOR ISRAELI AND NORWEGIAN CITIZENS
-

 Technology3 years ago
Technology3 years agoRNDcoin: Korea’s first blockchain project and a world-class cryptocurrency
-

 Uncategorized3 years ago
Uncategorized3 years agoAMERICAN VISA FOR NORWEGIAN AND JAPANESE CITIZENS
-
Lifestyle1 year ago
A Guide to Silverdaddies: What You Need to Know
-

 Fashion1 year ago
Fashion1 year agoGoda Perfume Reviews: Is It Worth Your Investment?
-

 Health3 years ago
Health3 years agoHealth Benefits Of Watermelon
-

 Home Improvement9 months ago
Home Improvement9 months agoArtificial Grass Designs: Perfect Solutions for Urban Backyards