Lifestyle
Navigating Tree Removal in Cross Junction: A Guide to Responsible Practices

Tree removal is a significant undertaking that requires careful consideration of environmental impact, legal regulations, and safety measures. In Cross Junction, a community nestled amidst the natural beauty of Virginia’s countryside, the process of tree removal is particularly sensitive due to the area’s lush landscapes and ecological diversity. Whether you’re a homeowner, developer, or property manager, understanding the nuances of tree removal in Cross Junction is crucial for preserving both the aesthetic appeal and environmental health of the region.
Importance of Responsible Tree Removal
Trees play a pivotal role in maintaining ecological balance, enhancing air quality, and providing habitat for wildlife. Therefore, the decision to remove a tree should never be taken lightly. In Cross Junction, where the scenic beauty is part of the community’s charm, responsible tree removal practices are essential to safeguarding the area’s natural heritage while accommodating necessary development and safety concerns.
Legal Considerations and Regulations
Before embarking on any tree removal project in Cross Junction, it’s imperative to familiarize yourself with local regulations and obtain any necessary permits. Regulations regarding tree removal can vary based on factors such as tree size, location, and environmental impact. The Frederick County government typically oversees tree removal permits, ensuring that any removal activities adhere to environmental protection laws and zoning ordinances.
Hiring Professional Tree Removal Services
For most tree removal projects in Cross Junction, engaging the services of a professional arborist or tree removal company is highly recommended. These professionals possess the expertise, equipment, and insurance necessary to safely and effectively remove trees while minimizing impact on surrounding vegetation and property. When selecting a tree removal service, consider their reputation, credentials, and commitment to environmental stewardship.
Environmental Impact and Mitigation Strategies
Mitigating the environmental impact of tree removal is a priority in Cross Junction. Strategies to minimize disruption include:
- Selective Cutting: Removing only trees that pose safety risks or are necessary for development, while preserving healthy trees and maintaining biodiversity.
- Replanting Initiatives: Compensating for tree removal by planting new trees in suitable locations, thereby restoring canopy cover and contributing to local ecosystem health.
- Erosion Control: Implementing erosion control measures to prevent soil degradation and protect water quality during and after tree removal activities.
Community Engagement and Consultation
In a community like Cross Junction, where residents value their natural surroundings, open communication and consultation with neighbors and local stakeholders are essential. Engaging community members in discussions about tree removal projects fosters transparency, addresses concerns, and promotes consensus on balancing development needs with environmental preservation.
Safety Precautions During Tree Removal
Safety is paramount during tree removal operations. Professional tree removal services adhere to industry standards and safety protocols to mitigate risks such as falling branches, equipment malfunctions, and injury to workers or bystanders. Homeowners should exercise caution and avoid attempting tree removal without proper training and equipment.
Utilizing Recycled Wood and Sustainable Practices
In Cross Junction, recycling and repurposing wood from removed trees are common practices that promote sustainability. Wood from removed trees can be used for lumber, firewood, mulch, or even artistic purposes, reducing waste and maximizing the utility of natural resources.
Conclusion
Tree removal in Cross Junction represents a delicate balance between development needs and environmental conservation. By adhering to legal regulations, hiring qualified professionals, mitigating environmental impact, and engaging the community, stakeholders can ensure that tree removal projects are conducted responsibly. Ultimately, preserving the scenic beauty and ecological health of Cross Junction requires thoughtful planning, collaboration, and a commitment to sustainable practices. Whether you’re planning a residential tree removal or a larger-scale development project, embracing responsible tree removal practices contributes to the long-term well-being and vibrancy of this picturesque community in Virginia’s Shenandoah Valley.
In conclusion, responsible tree removal in Cross Junction is not just about cutting down trees; it’s about preserving the natural environment and enhancing community resilience for future generations to enjoy.
Read More About the Website!
Lifestyle
Who is Karna: The Unsung Hero of the Mahabharata

Introduction
The epic Mahabharata is filled with legendary heroes, each with their own unique stories and struggles. Among them, Karna stands out as one of the most complex and fascinating characters. Known for his bravery, generosity, and loyalty, Karna’s life is a tale of courage, heartbreak, and resilience. In this article, we’ll explore everything about him from his mysterious birth to his legendary friendship with Duryodhana, and his role in the great battle of Kurukshetra. By the end, you’ll have a complete understanding of who Karna is and why he remains an enduring symbol of honor and sacrifice.
Karna’s Birth and Early Life
Karna was born to Kunti, the mother of the Pandavas, before her marriage. She invoked a divine mantra given by Sage Durvasa, and Karna was born with extraordinary powers from the Sun God, Surya. However, fearing social stigma, Kunti abandoned him, and he was adopted by a charioteer’s family. Despite growing up in humble surroundings, Karna displayed remarkable talent and courage from a young age.
His story teaches us about the unpredictability of life. Being born with greatness doesn’t always guarantee recognition. Karna’s early struggles shaped his character, instilling resilience, humility, and a deep understanding of hardship.
Karna’s Education and Skills
Karna’s thirst for knowledge was unquenchable. He sought training in archery and martial arts, but was often denied due to his perceived lower caste. Undeterred, he approached Parashurama, a great teacher, by claiming he was a Brahmin. Karna mastered advanced combat skills and weapons under his mentor’s guidance.
His dedication shows us that talent combined with determination can overcome social barriers. Karna became an exceptional warrior, known for his accuracy with arrows, strategic thinking, and unmatched courage in battle.
The Friendship Between Karna and Duryodhana
One of the defining aspects of Karna’s life was his deep friendship with Duryodhana, the Kaurava prince. Recognizing Karna’s potential, Duryodhana made him king of Anga, elevating his status. In return, Karna pledged unwavering loyalty to Duryodhana, even when it placed him against his own brothers, the Pandavas.
This relationship highlights the theme of loyalty and gratitude. Karna’s friendship teaches us that true allies stand by us in both triumph and adversity, even when the path is morally complex.
Karna’s Generosity and Virtues
Karna was famed not just for his martial prowess but also for his generosity. Known as Daanveer Karna, he never refused anyone who sought help, even during times of personal hardship. His magnanimity was so legendary that he gave away his divine armor and earrings, which protected him in battle, when asked.
This unparalleled generosity reflects Karna’s moral strength. It reminds us that true heroism is not just about winning battles but also about kindness, empathy, and selflessness.
Karna’s Complex Relationship with the Pandavas
Though Karna was the eldest of the Pandavas, he grew up unaware of his true heritage. This created a deep, tragic conflict when he faced his brothers on the battlefield. Karna’s sense of duty to Duryodhana often conflicted with his blood ties, making his life a story of loyalty versus righteousness.
His dilemma teaches us about the complexities of human relationships. Karna’s life shows that loyalty and love can sometimes pull us in opposite directions, challenging our morals and convictions.
The Curse of Karna
Karna’s life was marked by several curses, which shaped his destiny. One of the most notable curses came from Parashurama, who cursed him for deceiving him about his caste. Another curse involved a Brahmin whom Karna accidentally killed, leading to his eventual death in battle.
Despite these curses, Karna faced life with courage. His story emphasizes that adversity is inevitable, but how we respond defines our character. Karna’s endurance under relentless challenges is truly inspiring.
Karna in the Kurukshetra War
Karna played a pivotal role in the Kurukshetra War, fighting valiantly for the Kauravas. He faced off against some of the greatest warriors of the age, including Arjuna, his younger brother. Despite his unmatched skills, fate and the earlier curses led to his tragic death at Arjuna’s hands.
The battle highlights both his skill and tragic heroism. Karna’s courage in facing overwhelming odds makes him a timeless symbol of bravery, honor, and the human struggle against destiny.
Karna’s Legacy
Karna’s legacy transcends his death. He is celebrated as a symbol of courage, loyalty, and generosity. Many admire him for staying true to his principles, even when the world treated him unfairly. Karna’s story continues to inspire millions across generations, showing that true greatness comes from character, not just birth or status.
Lessons from Karna’s Life
Karna’s life offers powerful lessons for modern readers. His resilience teaches the value of perseverance, while his generosity reminds us to be selfless. His loyalty and moral dilemmas show the importance of integrity, even in the face of personal loss. Karna’s story encourages reflection on our choices, ethics, and the legacy we wish to leave.
Karna in Popular Culture
Karna’s influence extends beyond mythology. He has been depicted in numerous books, TV shows, movies, and plays. His character continues to captivate audiences due to his bravery, moral strength, and tragic life. Karna serves as a reminder that great stories endure because they reflect universal human experiences love, loyalty, courage, and tragedy.
FAQs About Karna
1. Who is Karna in Mahabharata?
Karna is the eldest son of Kunti and the Sun God, raised by a charioteer’s family, and a key warrior in the Mahabharata.
2. Why is Karna called Daanveer?
He is called Daanveer because of his unmatched generosity, giving away even his protective armor to help others.
3. Who were Karna’s friends?
Karna’s closest friend was Duryodhana, who supported him when society rejected him.
4. Did Karna know he was a Pandava?
He discovered his true heritage late in life, during the Kurukshetra War.
5. How did Karna die?
Karna was killed by Arjuna in the Kurukshetra War, influenced by curses and fate.
6. What can we learn from Karna?
His life teaches resilience, generosity, loyalty, and the importance of staying true to one’s values.
Conclusion
Karna is much more than a warrior; he is a symbol of honor, loyalty, and human resilience. His life reminds us that greatness is defined not by birth but by actions, values, and courage in adversity. Understanding who Karna is helps us appreciate the deeper moral and emotional lessons of the Mahabharata. His story continues to inspire, teaching timeless lessons about friendship, generosity, and facing life’s challenges with dignity.
Lifestyle
Dalai Lama Quotes: Short Teachings, Real Practice

Introduction
The Dalai Lama is one of the world’s most recognized spiritual teachers. His name is Tenzin Gyatso, and his life spans many decades of teaching. People turn to his short sayings for calm, guidance, and hope. This article collects clear, useful dalai lama quotes and explains why they matter. You will find simple explanations and practical ways to use the lines in life. I aim to write in a friendly, plain voice that is easy to follow. Each section pairs a quote with a short practice or reflection you can try. By the end, you will have tools to bring these words into daily habit.
Who is the Dalai Lama?
Tenzin Gyatso is the 14th Dalai Lama and was born in 1935. He became a symbol of peace and compassion for millions of people. His role grew from Tibetan Buddhist roots to a global moral voice. Short dalai lama quotes reflect his blend of spiritual depth and practical care. He speaks in plain language that many people can use and test. Knowing his background helps the sayings land more clearly in your life. This brief frame aims to help you use the words wisely and with respect. See the sayings as doors into a fuller teaching, not as the whole teaching.
Why these words resonate worldwide
Many dalai lama quotes feel simple and direct at first reading. The language is clear and easy to remember for many people. They often address common human needs like kindness and safety. The sayings connect inner training to everyday action and choices. This link makes them useful for both personal and public life. People from different cultures find these lines helpful and humane. That is why the quotes spread quickly on social media and in classrooms. Use them as starting points for habits that grow over time and deepen understanding.
Core themes in his teachings
You can find repeating themes in most dalai lama quotes. Compassion is at the center of his teachings and daily advice. Happiness as inner work is another major recurring point. Mindfulness, forgiveness, and ethical living also appear often in his lines. These themes make the sayings practical rather than only poetic. When you read a quote, look for which theme it supports. That will help you choose a small, related practice to try each day. Over weeks, this method turns short sayings into steady personal change.
How to use the lines in daily life
Using dalai lama quotes in daily life needs small, steady steps. Begin with one short line as a weekly focus to test ideas. Write the phrase on a sticky note and place it where you see it. Read it each morning and let it guide one small action each day. Try a short evening note to record what changed and what did not. Over weeks, small habits move words into real behavior and calm. This method helps you learn if a quote truly supports your life. Keep the practice simple and kind to yourself as you try it.
Short powerful quotes and what they mean
Here are a few short dalai lama quotes and what they can mean. Be kind whenever possible. It is always possible. See kindness as a practice you can repeat. Happiness is not something ready made. It comes from your own actions. This points to inner training and habits. If you want others to be happy, practice compassion. This links your joy to others’ good. Our prime purpose in life is to help others. That line calls for service and steady care. Each short saying is a spark to choose one small habit tied to it.
Quotes that teach compassion
Compassion shows up again and again in dalai lama quotes. He frames compassion as both feeling and helpful action. One short line states that love and compassion are necessities, not luxuries. That idea asks us to treat compassion as essential every day. Make compassion a habit with small acts of listening and care. Practice can be simple, like helping without being asked. Try a simple habit like listening without interrupting for one conversation each day. Notice how slowing down changes your view of another person. Practice small acts for a week and record any shifts in your mood.
Quotes on happiness and mental health
Many dalai lama quotes focus on happiness as a skill to train. He suggests happiness comes from inner habits more than external gains. This view helps when life feels unstable or full of stress. Short quotes can act as anchors for breath work and gratitude practice. Pair a line with three steady breaths whenever you feel anxious. Over time, such tiny routines build resilience and clearer attention. Use a phrase to remind you to pause before reacting. These small moves make inner calm more steady and reliable in daily life.
Leadership, ethics, and public life
Dalai Lama quotes on leadership often stress ethics over power. One clear idea is that inner peace supports better public choices. Leaders who act from kindness tend to make more humane policy. You can use a short quote as an ethical prompt in meetings. Ask, “Which choice grows care and lowers harm?” when planning actions. Turning a saying into a team question keeps ethics practical and visible. Even in business and civic life, simple ethical prompts can shift culture. Encourage small acts of service at work and notice the cumulative effect.
Context and common misunderstandings
Short lines can get shared without their fuller context and lose depth. Some dalai lama quotes come from longer talks or books where nuance exists. If you want to use a line deeply, read the original passage when possible. Context reveals the purpose, background, and the question the teacher answered. Learning that background prevents naive or sentimental uses of a quote. Take the time to read fuller sources when a saying feels important to you. Doing so builds respect for the tradition and keeps your use honest and helpful.
How to credit and share quotes correctly
Credit the Dalai Lama when you share his words on social media or in print. Add “— Dalai Lama (Tenzin Gyatso)” and, if known, the book or speech title. Citing the source honors the author and helps readers find reliable context. If you quote a long passage, check the publisher for permission to reuse it. Short phrases are often used freely, but transparency is best practice. Many people bookmark dalai lama quotes to return to later. Good credit builds trust and respects the teaching tradition behind the words. This small care keeps sharing fair and clear for everyone.
A short guided practice using a line
Try this short guided practice with one clear line today. Choose a simple phrase to repeat. For example, Be kind whenever possible. Sit upright for two minutes with feet flat and eyes lightly closed. Breathe and let the phrase move through your mind without force. Notice thoughts and feelings and do not follow them. After the sit, write one small thing you will do to act on the phrase. This exercise turns a saying into a living prompt for your day. If you keep it short, you are more likely to repeat it.
Living examples and modern uses
People use these sayings in classrooms, therapy, and community work around the world. Teachers use them to spark moral discussion with young students and adults. Therapists sometimes use short lines as entry points for values work. Leaders place these quotes in speeches to nudge ethical choices and care. Artists and writers quote them when they want to point to deeper values. Seeing varied uses shows how flexible a short, wise line can be in practice. Try borrowing a quote for a lesson, talk, or workshop with a clear practice attached.
Quick list of guiding sayings with prompts
A few guiding dalai lama quotes with tiny prompts can jumpstart practice. One line says that a true religion can be summed up as simple kindness. Prompt: Do one small kind act today. Another remark asks us to open to change while holding our values. Try a small new habit gently as the prompt suggests. A telling line reminds us that not getting what we want can become good luck. Reframe a recent loss by finding one new possibility in it. Try each prompt for three days and then pick the one that fits best.
Frequently Asked Questions
Are these quotes copyrighted and safe to share?
Are these quotes copyrighted and safe to share? Short quotations often fall under fair use, but rules differ by country. Many short phrases the Dalai Lama has used are widely quoted in public forums. For social sharing, include the author’s name and a source when possible. If you plan to publish a long passage, contact the book publisher for guidance on permissions. Being transparent about sources keeps sharing honest and fair for creators and readers. This approach balances respect for intellectual property with the public desire to learn from wise sayings.
Are they religious or useful for everyone?
Are they religious or useful for everyone? Many sayings grow from Buddhist teaching. Yet most lines use plain language and point to common human needs like kindness. This plain phrasing makes the quotes accessible across different faiths and cultures. You can use them in secular settings without adopting religious beliefs. Many people find the lines helpful when they want clearer habits and calm. Read a saying as a human prompt first, then explore its religious roots if you wish. That keeps use both respectful and practical.
How can I use quotes in teaching or therapy?
How can I use these quotes in teaching or therapy? Begin with short, clear lines that match your session goals. Use them as prompts for journaling, discussion, or role play in groups. Ask learners to reflect for five minutes and then share one action idea. In therapy, a quote can open a conversation about values and behavior experiments. Always pair a saying with small practices so it becomes real change. This method helps you turn a wise line into a tool for learning and healing.
Where can I find reliable collections of quotes?
Where can I find reliable collections of quotes? Look for books published by respected presses and credible translators. Official websites and academic translations often list verified lines with clear context. Avoid random social posts that show famous lines without any source. Reading longer works gives fuller meaning and reduces the risk of misinterpretation. When possible, choose editions with notes, dates, or translation credits. That deeper reading builds a firm and honest understanding of the sayings.
How do I avoid misusing quotes on social media?
How do I avoid misusing famous sayings on social media? Add context to show your intent and add a source when you can. Avoid attaching a quote to a political claim it did not support originally. Explain briefly why the line matters to your post or your readers. If you compress a long idea into a short line, warn readers about the simplification. Transparency prevents misunderstanding and keeps the message honest and helpful. Small explanations alongside quotes protect both the teaching and your credibility.
Can these quotes help with daily stress and anxiety?
Can these quotes help with daily stress and anxiety? Yes, when used as anchors for tiny, repeatable practices. A single short line can reorient attention toward kindness, breath, or a gentle pause. Pair a quote with three deep breaths or a short grounding pause in your day. Over time, these small moves build mental habits that ease stress and support focus. Use the lines as anchors rather than quick fixes. That steady approach helps new patterns form and improves well-being over time.
Conclusion
Dalai Lama teachings offer brief windows into a lived ethic of care and practice. They ask for inner work and small, steady action. Use one line as a weekly focus and pair it with small daily tests. Share quotes with credit and attach simple practices when you teach them to others. For deeper study, read longer works and trusted translations with context provided. May these lines help you grow kindness, calm, and practical wisdom in daily life. If a quote helped you, consider sharing the small practice you tried with friends or a group.
Lifestyle
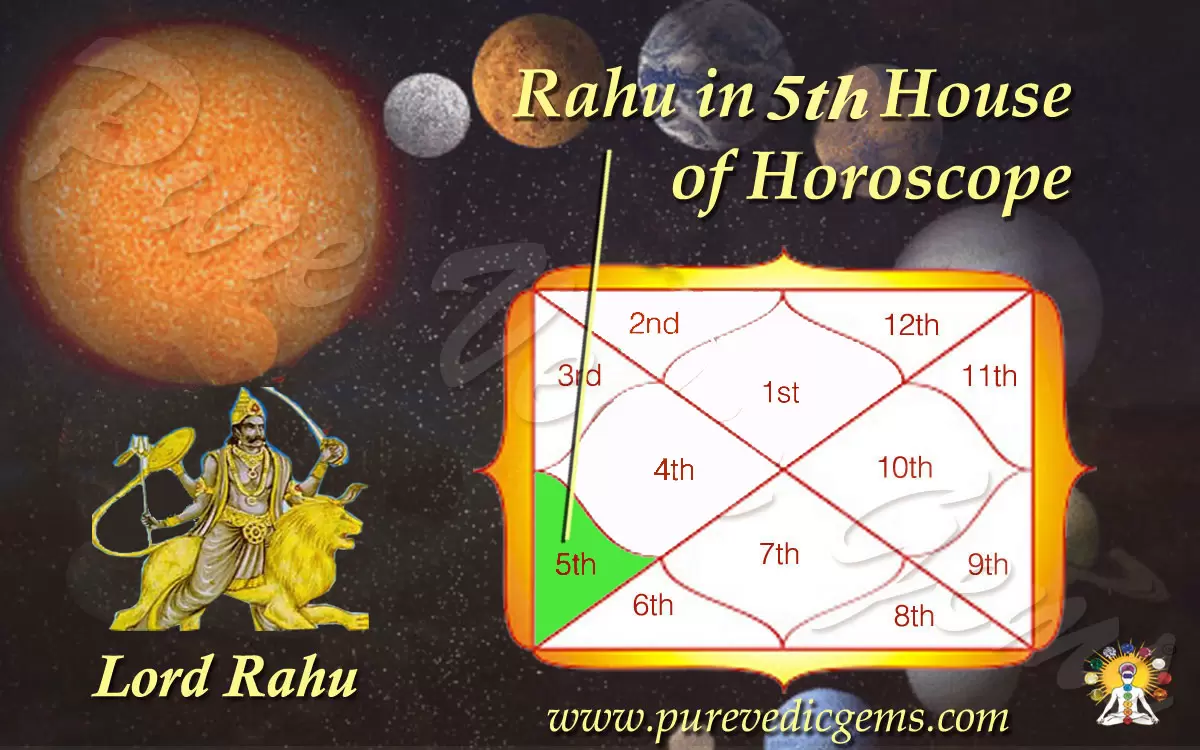
Rahu in 5th House — A Friendly, Practical Guide for Beginners
-

 Technology3 years ago
Technology3 years agoIs Camegle Legit Or A Scam?
-

 Travel3 years ago
Travel3 years agoNEW ZEALAND VISA FOR ISRAELI AND NORWEGIAN CITIZENS
-

 Uncategorized3 years ago
Uncategorized3 years agoAMERICAN VISA FOR NORWEGIAN AND JAPANESE CITIZENS
-

 Technology3 years ago
Technology3 years agoRNDcoin: Korea’s first blockchain project and a world-class cryptocurrency
-

 Fashion1 year ago
Fashion1 year agoGoda Perfume Reviews: Is It Worth Your Investment?
-

 Health3 years ago
Health3 years agoHealth Benefits Of Watermelon
-

 Home Improvement7 months ago
Home Improvement7 months agoArtificial Grass Designs: Perfect Solutions for Urban Backyards
-

 Fashion3 years ago
Fashion3 years agoBest Essentials Hoodies For Cold Weather