Technology
What are Malware and Examples?

Viruses, adware, rootkits, and other forms of malware are all forms of malicious software that are designed to cause harm to your computer. Fortunately, there are many ways to protect yourself against this danger.
Phishing Attacks
Typically, phishing attacks are conducted via email. In addition to exploiting known security vulnerabilities, phishing uses tactics such as misdirection, forgery, and lying to gain access to personal information. Besides stealing personal information, threat actors also install malware on the infected device.
The first step to protecting against phishing attacks is identifying the attack type. There are three direct phishing attacks: standard email, spear, and voice.
Spear phishing is a targeted email attack that targets specific individuals or organizations. It requires a lot of intelligence to pull off.
In this attack, the malicious actor sends a fraudulent email that appears to come from a trusted source. Often, this email will request the recipient to review a document or to provide account information. The sender may also ask the recipient to wire money.
The goal of a phishing attack is to get the victim to download or install malware on the infected machine. This can be done by sending links to password-protected documents or redirecting the link to a malicious website.
Malvertising
Using the Internet has become increasingly easy for criminals to get their hands on stolen information. Malvertising is one of the many ways criminals have taken advantage of this.
Malvertising is a form of cybercrime involving malware distribution through online ads. These ads are designed to look like regular advertisements but can infect users’ computers.
Malvertising often uses ad networks like Google to spread malicious ads. However, most website owners need to learn who buys ads next to their content.
These ads are very effective for hackers in spreading malware to users. In a typical malvertising campaign, the attackers choose a popular website or content to place their ads. They then use a “steganography” attack to redirect users to a spoofed website.
The ad may also direct users to a landing page that prompts them to install the software. This software could be spyware that spies on their activity or a keylogger that sends their login credentials to the hacker.
Computer viruses
Viruses are malicious programs that damage your computer, data, or software. They can also steal your private information. They can be distributed through email attachments, websites, and other methods. They can infect a Mac, Windows, Linux, or Android device. Computer viruses, worms, ransomware, and spyware are some examples of malware. These malicious programs steal, encrypt, and delete private information. They also change or hijack fundamental computer operations and track end users’ online behavior.
They have become so destructive that the annual cost of malware is estimated at over $55 billion. Sometimes, they can even disrupt your computer and make your system crash regularly.
The most common method of spreading a virus is via an email message. Some viruses can also attach themselves to legitimate software or software packs. These programs can be downloaded from the Internet, code repositories, or compromised application stores.
Other computer viruses include web scripting viruses, infecting a browser, and executing JavaScript. Another type of virus is a boot sector virus. This type of malicious software infects the master boot record on a hard drive or a USB thumb drive.
Adware
Whether browsing the Internet, downloading software, or reading emails, you’ve probably encountered malware or adware. Both are harmful to your computer and the privacy of your personal information.
When a user installs an adware program, it may change the homepage of the web browser, redirect users to a malicious website, or collect and store sensitive user information. The data collected by the adware can be shared with advertisers without the user’s knowledge or consent.
Adware may also generate revenue for the developer. This can come from two sources: the ads it displays and the clicks it generates. Typically, adware serves deceptive advertisements. Some adware, such as Rafotech’s Fireball, floods users with ads.
Some adware programs install new toolbars, extensions, and pop-up windows to a browser. These applications are usually bundled with free or fee-to-use software.
Some adware programs can add spyware and malicious programs to your system. Some adware can collect sensitive information like your bank account or credit card numbers. The adware’s authors can use these to track your activity and serve more targeted ads.
Rootkits
Originally, rootkits were maliciously modified administrative tools for Unix-like operating systems. These tools could be used to gain full system privileges and hide activity from standard operating system security tools.
Today, a more specialized type of rootkit has emerged. These programs are designed to take over the entire system, allowing an attacker to control the computer and perform malicious activities.
To install a rootkit, the hacker must have access to the system’s hardware. This makes them difficult to remove, although the good news is that they are relatively difficult to detect.
Malware distributors, cybercriminals, and APT groups often use these programs to gain computer control. They can be used to install spyware, ransomware, and other malicious software. They also act as keyloggers, allowing the hacker to record every key press.
Ransomware
Usually, ransomware is malicious software that encrypts or locks data on your computer. Then, it demands money in exchange for the decryption key. It can also block your access to your computer or device. Fortunately, you can fix the problem.
Typically, ransomware attacks are distributed through phishing emails. These malicious emails include a link that enables the download of a malicious program. Once the malware is downloaded, the attacker can exploit the system and network vulnerabilities to infect the victim’s machine.
The victim may have to pay hundreds of dollars in ransom to restore their files. Some malware encrypts files with asymmetric encryption. These files can only be opened with a mathematical key that the attacker knows. Once the victim pays the ransom, the encrypted data is unlocked.
Technology
Data Matrix Labels: The Complete Guide to 2D Barcode Technology

Introduction
Every day, billions of products move through global supply chains, each requiring precise identification and tracking. From tiny electronic components to life-saving medical devices, accurate labeling can mean the difference between seamless operations and costly errors. Data matrix labels have emerged as a powerful solution to these challenges, offering unparalleled data storage capacity in remarkably small spaces.
Unlike traditional barcodes that store information in parallel lines, data matrix labels use a two-dimensional grid of black and white squares to encode data. This compact format can hold up to 2,335 alphanumeric characters while occupying minimal surface area. The technology has revolutionized industries where space is premium and accuracy is non-negotiable.
This comprehensive guide explores everything you need to know about data matrix labels, from their technical specifications to real-world applications across various industries. Whether you’re considering implementing this technology or seeking to optimize existing systems, you’ll discover practical insights to make informed decisions.
What Are Data Matrix Labels?
Data matrix labels represent a type of two-dimensional barcode that stores information in a square or rectangular pattern of black and white cells. Developed by International Data Matrix Inc. in 1989, this technology was later released into the public domain in 2000, making it freely available for commercial use.
The structure consists of two key components: data regions containing the encoded information and finder patterns that help scanners locate and orient the code. The finder pattern appears as a solid black border on two adjacent sides, with alternating black and white squares forming the opposite borders.
Data matrix codes range in size from 10×10 to 144×144 cells, with each configuration optimized for different data capacities. The smallest versions can store up to 6 numeric characters, while the largest accommodate thousands of characters including numbers, letters, and special symbols.
These labels gained widespread adoption due to their error correction capabilities. Using Reed-Solomon error correction algorithms, data matrix codes remain readable even when up to 30% of the symbol is damaged or obscured. This resilience makes them ideal for harsh industrial environments where traditional barcodes might fail.
Why Use Data Matrix Labels?
Data matrix labels offer several compelling advantages over traditional identification methods, making them increasingly popular across diverse industries.
Superior Data Density
The most significant benefit lies in their exceptional data density. A data matrix label measuring just 2.5mm square can store the same information as a linear barcode requiring 25mm of space. This efficiency proves crucial when labeling small components like circuit boards, medical implants, or precision instruments where surface area is extremely limited.
Enhanced Accuracy and Reliability
Error correction technology ensures data integrity even under challenging conditions. Manufacturing environments often expose labels to heat, chemicals, abrasion, and moisture. Data matrix labels maintain readability through these conditions, reducing misreads that could disrupt production or compromise quality control.
Omnidirectional Reading
Unlike linear barcodes that require specific scanning angles, data matrix labels can be read from any direction. This flexibility speeds up scanning processes and reduces operator training requirements, particularly valuable in fast-paced environments like distribution centers or assembly lines.
Permanent Direct Part Marking
Data matrix technology enables direct marking onto products using laser etching, dot peening, or chemical etching. This permanent marking eliminates concerns about label adhesion failure and ensures traceability throughout a product’s entire lifecycle, even in extreme conditions.
Industries Using Data Matrix Labels
Data matrix labels have found widespread adoption across industries where precision, traceability, and reliability are paramount.
Aerospace and Defense
The aerospace industry relies heavily on data matrix labels for component traceability and maintenance tracking. Every critical part, from engine components to avionics, carries a data matrix code containing manufacturing details, batch information, and maintenance history. This comprehensive tracking system supports rigorous safety standards and enables rapid identification of affected parts during safety recalls or maintenance inspections.
Healthcare and Pharmaceuticals
Healthcare applications demand absolute accuracy in product identification. Data matrix labels on pharmaceutical packaging help prevent medication errors by encoding drug names, dosages, lot numbers, and expiration dates. Medical devices use these labels for unique device identification (UDI) compliance, supporting patient safety and post-market surveillance requirements.
Hospitals increasingly use data matrix labels for patient identification wristbands and specimen tracking, reducing the risk of mix-ups that could compromise patient care. The labels’ small size makes them practical for tiny samples and delicate medical instruments.
Electronics Manufacturing
The electronics industry leverages data matrix labels extensively for component traceability and quality control. Circuit boards, semiconductors, and electronic assemblies carry these codes to track manufacturing parameters, test results, and supply chain information. This detailed tracking supports quality assurance processes and enables rapid response to component defects or supply chain disruptions.
Automotive Manufacturing
Automotive manufacturers use data matrix labels throughout production processes to track parts, manage inventory, and ensure quality standards. Engine blocks, transmissions, and safety-critical components carry permanent data matrix markings that survive the vehicle’s entire operational life. This traceability supports warranty claims, recall management, and maintenance scheduling.
Food and Beverage Industry
Food producers increasingly adopt data matrix labels for lot tracking and supply chain transparency. These labels enable rapid tracing of ingredients and finished products, supporting food safety investigations and regulatory compliance. The labels’ durability makes them suitable for refrigerated and frozen products where condensation might compromise traditional labels.
How Data Matrix Labels Work
Understanding the technical aspects of data matrix labels helps optimize their implementation and troubleshoot common issues.
Encoding Process
Data matrix encoding follows standardized algorithms that convert input data into the characteristic black and white cell pattern. The process begins with data optimization, where the encoder selects the most efficient character set for the input information. Common encoding modes include ASCII for standard text, C40 for uppercase alphanumeric data, and Base 256 for binary information.
The encoder then applies Reed-Solomon error correction, adding redundant data that enables reconstruction of damaged or missing information. Higher error correction levels provide greater resilience but reduce data capacity, requiring careful balance based on application requirements.
Reading and Verification
Modern data matrix readers use advanced image processing algorithms to locate, decode, and verify codes. The process begins with image acquisition using cameras or laser scanners, followed by pattern recognition to identify the finder patterns and determine code orientation.
Decoding algorithms extract the encoded data and apply error correction as needed. Verification systems can assess code quality using standardized grading parameters including symbol contrast, modulation, and decode success rates.
Print Quality Considerations
Successful data matrix implementation requires attention to print quality parameters. Cell size, contrast ratio, and edge definition significantly impact readability. Industry standards specify minimum requirements for these parameters, but optimal settings depend on specific application conditions including lighting, scanning distance, and environmental factors.
Common Challenges and Solutions
Despite their robust design, data matrix labels can present implementation challenges that require careful consideration and planning.
Print Quality Issues
Poor print quality represents the most common cause of data matrix reading failures. Insufficient contrast between black and white cells, blurred edges, or inconsistent cell sizes can prevent successful decoding. Solutions include regular printer maintenance, proper substrate selection, and implementing quality control checks during production.
Laser marking systems require calibration to achieve optimal power and speed settings for different materials. Too little power creates insufficient contrast, while excessive power can cause thermal damage that distorts cell geometry.
Environmental Damage
Harsh environmental conditions can degrade data matrix labels over time. Chemical exposure, abrasion, and temperature cycling can fade markings or create false patterns that interfere with reading. Selecting appropriate marking methods and protective coatings helps maintain readability throughout the product lifecycle.
For permanent direct part marking applications, material compatibility testing ensures optimal results. Different substrates respond differently to various marking technologies, requiring application-specific optimization.
Reading Distance and Lighting
Optimal reading performance requires appropriate scanner selection and setup. Reading distance, lighting conditions, and angle of approach all influence success rates. Fixed-mount scanners offer consistent performance for automated applications, while handheld readers provide flexibility for manual operations.
Proper lighting eliminates shadows and reflections that can interfere with image acquisition. LED illumination systems provide consistent, uniform lighting that enhances reading reliability across various environmental conditions.
Future Trends in Data Matrix Technology
Data matrix technology continues evolving to meet emerging industry requirements and leverage advancing capabilities.
Enhanced Data Capacity
Researchers are developing advanced encoding algorithms that increase data capacity without expanding symbol size. These improvements support applications requiring extensive information storage in minimal space, such as IoT devices and miniaturized medical implants.
Integration with Digital Technologies
Data matrix labels increasingly serve as bridges between physical products and digital information systems. Scanning a data matrix code can link to cloud-based databases containing real-time information about product status, maintenance requirements, or supply chain updates.
Blockchain integration offers immutable traceability records, supporting authenticity verification and supply chain transparency initiatives. This combination of physical marking and digital verification creates robust anti-counterfeiting solutions.
Advanced Materials and Marking Methods
New marking technologies enable data matrix creation on previously challenging materials and surfaces. Femtosecond laser systems can create high contrast markings on transparent materials, while advanced inks provide enhanced durability and contrast on flexible substrates.
Smart materials that change appearance under specific conditions could enable dynamic data matrix labels that display different information based on environmental factors or product status.
Implementing Data Matrix Labels Successfully
Successful data matrix implementation requires comprehensive planning that addresses technical, operational, and economic considerations. Start by clearly defining your traceability requirements and identifying the specific information that needs encoding. This analysis guides decisions about code size, data capacity, and marking method selection.
Pilot testing proves crucial for validating performance under actual operating conditions. Test various marking methods, substrates, and environmental conditions to identify optimal configurations before full-scale deployment. This approach minimizes implementation risks and ensures reliable long-term performance.
Training personnel on proper handling, scanning techniques, and troubleshooting procedures supports consistent results. Regular system maintenance and periodic quality assessments help maintain optimal performance over time.
Data matrix labels represent a mature, reliable technology that continues advancing to meet evolving industry needs. Their combination of high data density, durability, and reading flexibility makes them ideal for applications requiring precise identification and traceability. As industries increasingly emphasize supply chain transparency and product authentication, data matrix labels will play an increasingly important role in connecting physical products with digital information systems.
Frequently Asked Questions
What’s the difference between data matrix and QR codes?
Data matrix codes excel in industrial applications requiring small size and durability, while QR codes work better for consumer applications requiring larger data capacity and smartphone compatibility. Data matrix codes typically handle harsh environments better due to their robust error correction and compact design.
How small can data matrix labels be printed?
The minimum practical size depends on printing method and reading requirements. Laser marking can create readable codes as small as 1mm square, while inkjet printing typically requires larger sizes for reliable reading. Always test specific combinations of marking method, material, and reading equipment to determine practical limits.
Can data matrix labels be read if partially damaged?
Yes, Reed-Solomon error correction enables reading even when up to 30% of the code is damaged or obscured. The actual tolerance depends on the specific damage pattern and error correction level used during encoding.
What equipment is needed to read data matrix labels?
Data matrix reading requires specialized scanners with image-based decoding capabilities. Options range from handheld readers for manual scanning to fixed-mount industrial scanners for automated applications. Smartphone apps can read some data matrix codes, but industrial applications typically require dedicated equipment for reliable performance.
How do I choose the right data matrix size for my application?
Consider the amount of data to encode, available space for marking, and reading distance requirements. Smaller codes suit applications with limited space but may require closer reading distances. Larger codes accommodate more data and enable reading from greater distances but require more surface area.
Technology
How to get in touch everythingnew.net

Introduction
Looking to connect with the innovative minds behind get in touch everythingnew.net? This comprehensive guide will walk you through all the ways to reach out to this dynamic platform that serves as your hub for the latest trends in creativity, business, and technology.
EverythingNew.net positions itself as more than just a website it’s a “circus of innovation” where creativity meets cutting-edge technology. Whether you’re seeking collaboration opportunities, have questions about their content, or want to engage with their community, knowing how to get in touch effectively can open doors to meaningful connections.
This guide covers everything from direct contact methods to social media engagement strategies, ensuring you can connect with EverythingNew.net in the way that best suits your needs.
Understanding EverythingNew.net’s Mission
Before reaching out, it’s helpful to understand what get in touch everythingnew.net represents. The platform describes itself as “the place where creativity never gets old,” offering insights across three main categories:
Creatives: A space where creativity knows no bounds, featuring content that explores innovation and expression through various mediums.
Business: Strategic insights focusing on market dynamics, visionary leadership, and sustainable growth in competitive landscapes.
Technology: Pioneering advancements that redefine possibilities, from AI solutions to transformative digital experiences.
Understanding these focus areas helps you tailor your communication and increases the likelihood of a meaningful response.
Primary Contact Methods
Newsletter Subscription for Updates
The most straightforward way to stay connected with get in touch everythingnew.net is through their newsletter subscription. Located prominently on their homepage, the newsletter signup allows you to:
- Receive the latest insights and trends in creativity, business, and technology
- Stay updated on new content releases
- Get priority access to special announcements
To subscribe, simply visit the homepage and enter your email address in the subscription box titled “Discover get in touch everythingnew.net: Creatives, Business, Technology.”
Direct Website Engagement
While specific contact email addresses aren’t prominently displayed on the main page, website engagement remains a primary touchpoint. The site features:
- Comment sections on blog posts where you can engage directly with content
- Interactive elements that encourage reader participation
- Multiple content categories that allow you to find relevant discussion topics
Content-Specific Outreach
EverythingNew.net features content from specific contributors, including:
- Innovation Pulse by Falnosel Homtuk: Covering topics from Singapore’s online casino landscape to educational facility hygiene
- Business Strategies from Selnorin Caldor: Focusing on marketing innovations and business banking solutions
- Technology insights: Spanning digital storytelling, cybersecurity, and emerging AI technologies
When reaching out about specific content areas, reference the relevant contributor or content category to ensure your message reaches the right person.
Social Media Engagement Strategies
Finding Their Social Presence
While specific social media handles aren’t listed on the scraped content, most digital platforms like get in touch get in touch everythingnew.net maintain active social media presences. Look for:
- LinkedIn profiles for professional networking and business inquiries
- Twitter accounts for real-time updates and quick interactions
- Facebook pages for community building and longer-form discussions
- Instagram for visual content and behind-the-scenes insights
Effective Social Media Outreach
When engaging on social platforms:
- Share relevant content: Repost their articles with thoughtful commentary
- Tag appropriately: Use relevant hashtags and tag the platform when sharing
- Engage authentically: Comment meaningfully on their posts rather than just liking
- Share your expertise: Contribute valuable insights related to their content themes
Professional Networking Opportunities
Industry Events and Conferences
Given get in touch everythingnew.net focus on innovation and technology, team members likely attend:
- Technology conferences and innovation summits
- Business networking events
- Creative industry gatherings
- Digital marketing conferences
Research these events and look for get in touch everythingnew.net representatives or sponsored content.
Content Collaboration
The platform regularly features diverse content across multiple categories, suggesting they’re open to:
- Guest posting opportunities
- Expert interviews
- Collaborative content creation
- Industry partnership discussions
When proposing collaboration, clearly outline:
- Your expertise and relevant background
- How your content aligns with their mission
- Specific value you can provide to their audience
- Examples of your previous work
Best Practices for Initial Contact
Crafting Your Message
When reaching out to get in touch everythingnew.net:
Be Specific: Reference particular articles or content areas that resonate with your inquiry.
Show Value: Explain what you can offer rather than what you want to gain.
Keep It Professional: Match their innovative yet professional tone.
Include Credentials: Briefly mention relevant experience or expertise.
Timing Your Outreach
Consider these factors when timing your contact:
- Business hours for professional inquiries
- Content publication schedules for timely responses
- Industry news cycles that might affect their availability
- Seasonal considerations for business-focused communications
Following Up Effectively
Persistence vs. Patience
Strike the right balance by:
- Waiting at least one week before following up on initial contact
- Providing additional value in follow-up messages
- Respecting their response time and workload
- Maintaining professionalism throughout the process
Building Long-term Relationships
Focus on relationship building rather than one-time interactions:
- Regularly engage with their content
- Share their articles within your network
- Provide feedback and constructive commentary
- Suggest story ideas or industry insights
Frequently Asked Questions
How quickly can I expect a response from EverythingNew.net?
Response times vary depending on the contact method and nature of your inquiry. Newsletter responses and general inquiries may take several business days, while social media interactions often receive quicker acknowledgment.
What types of content does get in touch everythingnew.net typically accept for guest posting?
Based on their existing content, they appear interested in innovative perspectives on technology, creative business strategies, and emerging industry trends. Content should be well-researched, professionally written, and aligned with their forward-thinking approach.
Can I pitch product reviews or sponsored content?
While the site features various product and service discussions, any commercial partnerships should be disclosed upfront. Focus on providing genuine value to their audience rather than purely promotional content.
How can I stay updated on new content and opportunities?
Subscribe to their newsletter and follow their social media channels. Regular engagement with their content also increases visibility for potential collaboration opportunities.
Building Meaningful Connections
Getting in touch with get in touch everythingnew.net successfully requires understanding their mission, respecting their professional approach, and providing genuine value. Whether you’re seeking to collaborate, learn, or simply connect with like-minded innovators, the key lies in authentic engagement and patience.
Remember that get in touch everythingnew.net positions itself as a hub for innovation and creativity. Your outreach should reflect these values while demonstrating how you can contribute to their community of forward-thinking individuals.
Start with their newsletter subscription to understand their content style and frequency, then engage meaningfully with their existing content before reaching out with specific proposals or questions. This approach shows respect for their work and increases your chances of building a lasting professional relationship.
Technology
Word Syllable Programs: Your Complete Guide to Better Reading
Introduction
Reading fluency remains one of the most critical skills students need to develop, yet many educators struggle to find effective tools that break down complex words into manageable parts. Word syllable programs have emerged as powerful educational technology solutions that help students decode unfamiliar words by teaching them to recognize syllable patterns and divisions.
These specialized software applications and digital tools use systematic approaches to teach syllable recognition, helping students improve their reading comprehension, pronunciation, and overall literacy skills. Whether you’re a teacher working with struggling readers, a parent supporting your child’s learning journey, or a reading specialist seeking evidence-based interventions, understanding how word syllable programs work can transform your approach to reading instruction.
Research consistently shows that students who master syllable division strategies read more fluently and comprehend text more effectively. With the right program, learners can develop the phonological awareness skills they need to tackle multi-syllabic words with confidence, setting the foundation for lifelong reading success.
Benefits of Using Word Syllable Programs
Word syllable programs offer numerous advantages that extend far beyond simple word division. These tools provide structured, systematic instruction that helps students develop essential reading skills while building confidence in their abilities.
Enhanced Reading Fluency
Students who use syllable programs typically show significant improvements in reading speed and accuracy. By learning to break words into smaller, manageable chunks, readers can decode unfamiliar terms more quickly and maintain better reading flow. This improved fluency allows students to focus more cognitive energy on comprehension rather than struggling with individual words.
Improved Spelling and Writing Skills
Understanding syllable patterns directly translates to better spelling abilities. When students recognize common syllable types and division rules, they can apply these patterns to spell new words correctly. This knowledge also supports writing development, as students become more confident using sophisticated vocabulary in their compositions.
Stronger Phonological Awareness
Syllable programs strengthen students’ ability to hear and manipulate sounds within words, a critical foundation skill for reading success. This enhanced phonological awareness supports not only reading development but also helps students with language processing challenges develop stronger literacy skills.
Increased Reading Confidence
Many students who struggle with reading avoid challenging texts because they feel overwhelmed by long, unfamiliar words. Syllable programs provide students with concrete strategies for tackling difficult vocabulary, reducing anxiety and increasing willingness to engage with more complex reading materials.
Key Features to Look for in a Word Syllable Program
Selecting an effective word syllable program requires careful consideration of several essential features that support comprehensive learning and long-term skill development.
Systematic Syllable Type Instruction
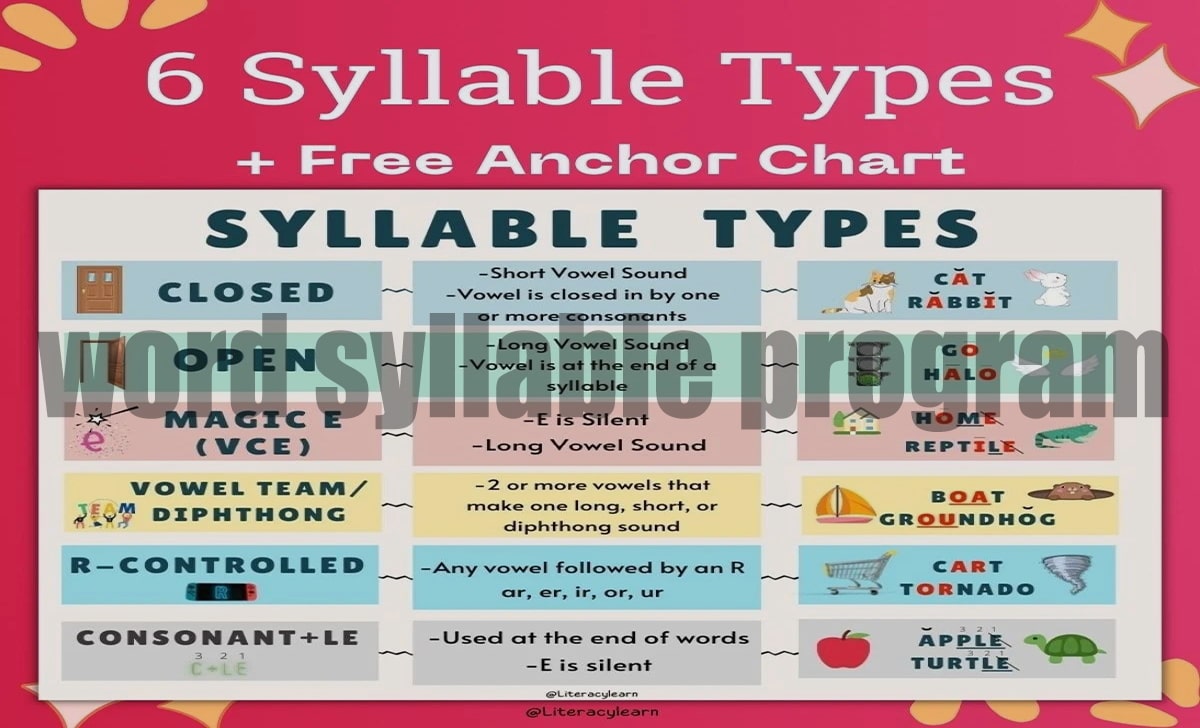
The most effective programs teach the six syllable types systematically: closed, open, vowel-consonant-e, vowel teams, r-controlled, and consonant-le. Look for programs that introduce these patterns in a logical sequence and provide ample practice opportunities for each type.
Interactive Learning Activities
Quality programs incorporate engaging, interactive elements that maintain student interest while reinforcing learning. Features might include drag-and-drop exercises, audio pronunciation guides, visual highlighting of syllable divisions, and gamified practice sessions that motivate continued engagement.
Progress Tracking and Assessment Tools
Robust data collection capabilities allow educators and parents to monitor student progress, identify areas needing additional support, and celebrate achievements. Look for programs that provide detailed reports on accuracy rates, completion times, and skill mastery levels.
Differentiated Instruction Options
Effective programs offer multiple difficulty levels and can adapt to individual student needs. This might include adjustable pacing, varied practice activities, and the ability to focus on specific syllable types or word patterns based on assessment results.
Multi-Sensory Learning Support
Programs that incorporate visual, auditory, and kinesthetic learning elements tend to be more effective for diverse learners. Features might include color-coding for different syllable types, audio pronunciation support, and hands-on manipulation activities.
Top Word Syllable Programs on the Market
Several high-quality word syllable programs have gained recognition for their effectiveness and user-friendly design. Each offers unique strengths that may appeal to different learning environments and student needs.
Reading A-Z’s Syllable Patterns
This comprehensive program integrates syllable instruction with broader reading curriculum, offering leveled texts and systematic skill development. The platform provides extensive teacher resources and aligns with common core standards, making it popular in classroom settings.
Lexia Core5 Reading
Known for its adaptive technology, Lexia Core5 includes robust syllable instruction within its comprehensive reading program. The software adjusts difficulty based on student performance and provides detailed progress monitoring tools for educators.
Wilson Reading System
While primarily known as a structured literacy program, Wilson includes strong syllable instruction components. The program follows a systematic, cumulative approach that’s particularly effective for students with dyslexia and other reading challenges.
Syllable Safari
This game-based program appeals to younger learners through its engaging animal-themed interface. Students practice syllable counting and division while progressing through various safari adventures, making learning feel like play.
How to Choose the Right Program for Your Needs
Selecting the most appropriate word syllable program requires careful assessment of your specific situation, student needs, and available resources.
Assess Student Skill Levels
Begin by evaluating current student abilities through informal assessments or standardized reading measures. Identify specific areas of need, such as single-syllable decoding, multi-syllabic word attack skills, or syllable pattern recognition. This information will help you choose programs that target appropriate skill levels.
Consider Implementation Context
Think about where and how the program will be used. Classroom implementation may require different features than home use or small-group intervention settings. Consider factors such as technology requirements, internet connectivity, and the need for progress monitoring tools.
Evaluate Budget and Resources
Program costs vary significantly, from free online resources to comprehensive subscription-based platforms. Consider not only initial costs but also ongoing subscription fees, training requirements, and technical support needs when making your decision.
Review Research and Evidence
Look for programs with documented effectiveness through peer-reviewed research or independent studies. Check for alignment with evidence-based reading instruction principles and examine user reviews from similar educational contexts.
Tips for Effective Use of Word Syllable Programs
Maximizing the benefits of word syllable programs requires thoughtful implementation and consistent use of best practices that support student learning and engagement.
Establish Consistent Routines
Create regular practice schedules that allow students to build skills progressively over time. Short, frequent sessions often prove more effective than longer, less frequent practice periods. Aim for 10-15 minute daily sessions rather than hour-long weekly practices.
Combine Digital and Hands-On Activities
While syllable programs provide excellent digital practice, supplement this learning with physical manipulation activities. Use wooden blocks, clapping exercises, or paper-and-pencil activities to reinforce concepts learned through the program.
Connect to Real Reading
Help students transfer their syllable skills to authentic reading experiences by explicitly connecting program lessons to books and texts they’re reading. Point out syllable patterns in context and encourage students to apply their strategies during independent reading time.
Provide Explicit Instruction
Don’t rely solely on the program to teach syllable concepts. Provide direct instruction about syllable types, division rules, and application strategies before students practice independently with the software.
Case Studies: Success Stories with Word Syllable Programs
Real-world examples demonstrate the transformative potential of well-implemented word syllable programs across diverse educational settings and student populations.
Elementary School Reading Intervention
Roosevelt Elementary implemented a school-wide syllable program for students reading below grade level. After one academic year, participating students showed an average reading growth of 1.5 grade levels, with 78% of participants reaching grade-level expectations. Teachers reported increased student confidence and willingness to attempt challenging words during classroom reading activities.
Middle School Special Education Support
Jefferson Middle School used targeted syllable instruction to support students with learning disabilities. The program helped reduce reading anxiety while improving decoding accuracy by an average of 35% over six months. Students particularly benefited from the multi-sensory features and self-paced learning options.
Home Learning Success
The Martinez family used a syllable program to support their struggling reader at home. Combined with regular reading practice, their child improved from a first-grade to third-grade reading level over eight months of consistent use. The child’s increased confidence led to voluntary independent reading for the first time.
Future Trends in Word Syllable Technology
Educational technology continues evolving rapidly, bringing exciting possibilities for enhanced syllable instruction and reading development support.
Artificial Intelligence Integration
AI-powered programs are beginning to offer more sophisticated adaptive learning experiences, adjusting not only difficulty levels but also instructional approaches based on individual learning patterns. These systems can identify specific student challenges and provide targeted interventions automatically.
Virtual and Augmented Reality Applications
Emerging VR and AR technologies promise immersive learning experiences that could make syllable instruction more engaging and memorable. Students might manipulate virtual word parts or practice syllable division in game-like environments that respond to their movements and choices.
Enhanced Speech Recognition
Improved speech recognition technology will likely enable more sophisticated pronunciation practice and feedback, helping students not only recognize syllable patterns but also produce them accurately in speech.
Cross-Platform Integration
Future programs will likely offer better integration with learning management systems, digital libraries, and assessment platforms, creating more seamless educational experiences for both students and educators.
Frequently Asked Questions
What age group benefits most from word syllable programs?
Word syllable programs are most effective for students in grades 2-6, typically ages 7-12, when children are developing advanced decoding skills. However, struggling readers of any age can benefit from systematic syllable instruction.
How long should students use a syllable program daily?
Research suggests 10-15 minutes of daily practice provides optimal results without causing fatigue or loss of engagement. Consistency matters more than duration for skill development.
Can syllable programs replace traditional reading instruction?
No, syllable programs should supplement, not replace, comprehensive reading instruction. They work best when integrated with phonics instruction, vocabulary development, and regular reading practice.
Are these programs effective for students with dyslexia?
Yes, many students with dyslexia benefit significantly from structured syllable instruction. The systematic, multi-sensory approach used in quality programs aligns well with evidence-based dyslexia interventions.
How quickly can students expect to see improvement?
Most students show measurable progress within 4-6 weeks of consistent use, with significant improvements typically evident after 2-3 months of regular practice.
Building Stronger Readers Through Strategic Implementation
Word syllable programs represent powerful tools for developing reading proficiency, but their effectiveness depends largely on thoughtful selection and implementation. The most successful outcomes occur when educators choose programs aligned with student needs, provide explicit instruction alongside digital practice, and maintain consistent implementation over time.
As educational technology continues advancing, these programs will likely become even more sophisticated and effective. However, the fundamental principles of systematic instruction, regular practice, and explicit strategy teaching will remain central to reading success.
Whether you’re supporting struggling readers, enhancing classroom instruction, or building foundational skills, word syllable programs can provide the structured practice students need to become confident, fluent readers. Take time to evaluate your specific needs, explore available options, and choose a program that aligns with your educational goals and student requirements.
-

 Travel3 years ago
Travel3 years agoNEW ZEALAND VISA FOR ISRAELI AND NORWEGIAN CITIZENS
-

 Technology3 years ago
Technology3 years agoIs Camegle Legit Or A Scam?
-

 Uncategorized3 years ago
Uncategorized3 years agoAMERICAN VISA FOR NORWEGIAN AND JAPANESE CITIZENS
-

 Health3 years ago
Health3 years agoHealth Benefits Of Watermelon
-

 Home Improvement5 months ago
Home Improvement5 months agoArtificial Grass Designs: Perfect Solutions for Urban Backyards
-

 Fashion2 years ago
Fashion2 years agoBest Essentials Hoodies For Cold Weather
-

 Uncategorized3 years ago
Uncategorized3 years agoHow can I write a well-structured blog post?
-

 Technology1 year ago
Technology1 year agoImagine a World Transformed by Technology and Innovation of 2023-1954